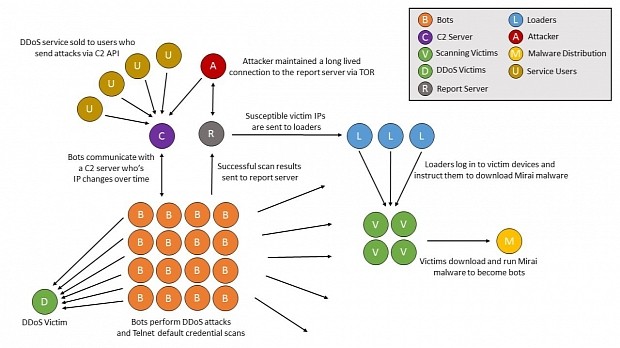
To no one's surprise, the release of the Mirai malware source code has resulted in other crooks creating their own variants, infecting new devices, and more than doubling the size of the original Mirai botnet.
This falls exactly into the plans of Anna-senpai, the nickname used by Mirai's author, who hoped that others would take his malware and create new botnets that will help him conceal his mega-botnet, the one he used to launch the biggest DDoS attacks known today.
Despite his attempt to hide his botnet from security firms and law enforcement, his efforts seem to have failed, with several cyber-security vendors issuing detailed reports on the botnet's activity and modus operandi.
New Mirai malware variants double botnet's size
One of the most recent reports is from Level 3, the company that tied the OVH and KrebsOnSecurity attacks to the Mirai botnet.
Level 3 says the number of Mirai-infected devices has gone up from 213,000 to 493,000, all in the span of two weeks since Anna-senpai released the malware's source code.
The current total Mirai botnet count includes not only the original Mirai bots but also other variations created and launched by different groups.
Nevertheless, this number includes only those botnets where researchers could identify Mirai-specific behavior. Smaller parts of Mirai were most likely absorbed in other IoT malware and will have a different impact on the IoT botnet landscape, albeit harder to quantify.
New Mirai botnets are already up and running
Level 3, who's been tracking the original Mirai botnet, says that Anna-senpai seems to have operated his botnet from the santasbigcandycane.cx domain, where he hosted the main command and control server.
Since the beginning of the month, when he open-sourced Mirai, new master C&C servers have been popping up in other places.
For example, a new Mirai botnet appeared and is now managed via the xf0.pw domain. Level 3 says that, previously, an IP associated with this domain was used to control a DDoS botnet created with the Gafgyt malware as recently as August 2016, showing that a skilled and experienced malware author is behind the botnet, a worrisome observation for the rest of us.
Another Mirai clone also appeared on October 3. Level 3 says this botnet appears to be controlled from two domains, at imscaredaf.xyz, and swinginwithme.ru.
Researchers say this variant had a "slightly different network behavior when compared to the original Mirai variant," and mixed some code from the Gafgyt IoT malware.
Mixing malware is a regular practice in the malware scene, especially for IoT malware. The Gafgyt malware, which leaked some years ago, also has hundreds of different versions created by different threat groups. Mirai is on schedule to feature just as many variants as Gafgyt, if not more, with crooks opting to build new malware on top of it due to its proven success.
80% of Mirai bots are DVR systems
As for infected targets, these new botnets continued to infect the same devices, with over 80 percent of all bots being DVRs, and the rest made up of routers, IP cameras, and regular Linux servers.
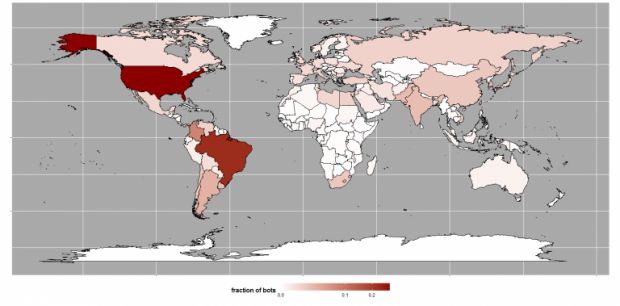
Below is a map of where most Mirai bots are located, with the US accounting for 29 percent of all infected systems, followed by Brazil with 23 percent, and Colombia with 8 percent.
 14 DAY TRIAL //
14 DAY TRIAL //