For the past years, F-Secure researchers have gathered data on a group of hackers that have been targeting Western businesses and governments, in what seems to be a pro-Russian cyber-espionage campaign.
For the past seven years, security researchers have been observing the actions of an advanced threat group called APT29, which included attacks on numerous targets in the EU, Asia, and the US.
The group was dubbed The Dukes by F-Secure's team, mainly because of a "smash-and-grab" bold approach to hacking, which didn't include any attempts of hiding their tracks.
The Dukes seem to have the same interests at heart as the Russian government
This fearless MO (modus operandi, method of operation), as F-Secure hints, may have been because of their ties to the Russian government, which is supposed to be providing them with financial backing and legal protection.
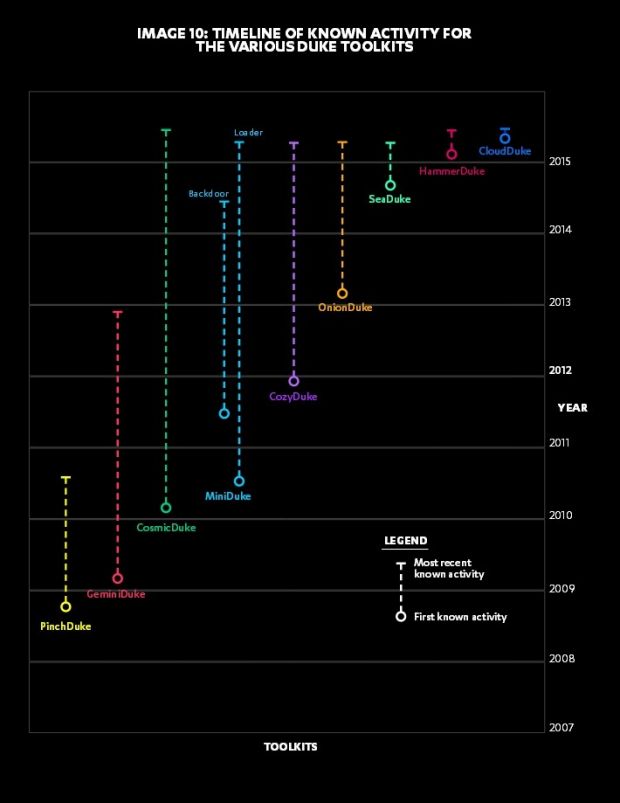
This allowed the group to amass a huge hacking arsenal, one that includes hacking tools like: MiniDuke, CosmicDuke, CozyDuke, CloudDuke, SeaDuke, HammerDuke, PinchDuke, OnionDuke, and GeminiDuke.
"In recent years, the Dukes have engaged in apparently biannual large-scale spear-phishing campaigns against hundreds or even thousands of recipients associated with governmental institutions and affiliated organizations," say F-Secure researchers.
Additionally, the group sometimes also seems interested in smaller targets as well, which coincidentally or not, aligns with known foreign and security policy interests the Russian Federation may have at that time.
| Malware Name | Activity Timeline | Toolset Components |
|---|---|---|
| PinchDuke | November 2008 - Summer 2010 | Multiple loaders Information stealer |
| GeminiDuke | January 2009 - December 2012 | Loader Information stealer Multiple persistence components |
| CosmicDuke (Tinybaron, BotgenStudios, NemesisGemina) | January 2010 - Summer 2015 | Information stealer Multiple loaders Privilege escalation component Multiple persistence components |
| MiniDuke | July 2010 - Spring 2015 | Downloader Backdoor Loader |
| CozyDuke (CozyBear, CozyCar, Cozer, EuroAPT) | January 2010 - Spring 2015 | Dropper Modular backdoor Multiple persistence components Screenshot module Password stealing module Password hash stealing module Information gathering module |
| OnionDuke | February 2013 - Spring 2015 | Dropper Loader Multiple modular core components DDOS module Password stealing module Information gathering module Social network spamming module |
| SeaDuke (SeaDaddy, SeaDask) | October 2014 - Spring 2015 | Backdoor |
| HammerDuke (Netduke, HAMMERTOSS) | January 2015 - Summer 2015 | Backdoor |
| CloudDuke (MiniDionis, CloudLook) | June 2015 - Summer 2015 | Downloader Loader Two backdoor variants |
Despite the fact that most of these tools have been exposed by one or multiple security firms in the past, F-Secure has seen that the group has never shied away from using them even days after they have been publicly uncovered.
Acting brazenly in the face of security firms and confident in their hacking skills, the group has always managed to retool their arsenal, managing to go back into the shadows every time after they have been uncovered.
The full The Dukes, 7 years of Russian cyberespionage report, is available on F-Secure's site.

 14 DAY TRIAL //
14 DAY TRIAL //