At the end of February 2015, Europol in collaboration with multiple security vendors sinkholed the C&C servers of the Ramnit botnet, used for financial fraud.
Now, ten months later, IBM's X-Force Threat Intelligence team is reporting that the cyber-gang behind the first botnet has slowly started building a second version of the botnet, using malicious ads to infect users with their banking trojan.
Ramnit v1 is still down
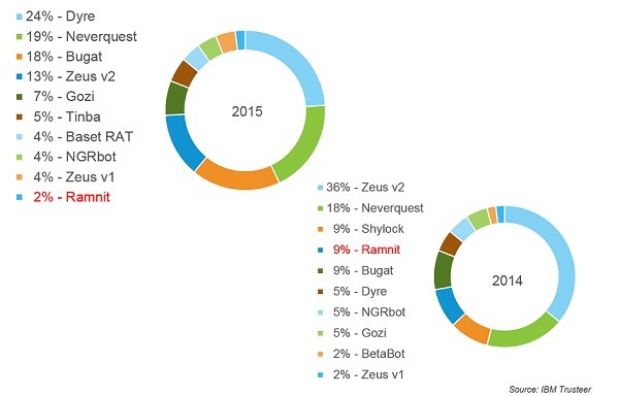
Ramnit made its debut on the cyber-crime scene in 2010 and slowly grew to be the fourth largest financial fraud botnet at the end of 2014, behind GameOver Zeus, Neverquest (Vawtrack), and Shylock.
Mainly targeting users in English-speaking countries like the US, Australia, and the UK, the botnet quickly got on the radar of cyber-security companies like Microsoft, Symantec, and AnubisNetworks, who collaborated with Europol’s European Cybercrime Centre (EC3) and had Ramnit taken down by sabotaging its main server.
IBM researchers report that the C&C server of the Ramnit v1 botnet is still sending out instructions, but because of Europol's efforts, these commands never reach any of the infected computers.
Botnet operators started from scratch with Ramnit v2
But this doesn't matter, since Ramnit's creators seem to have also abandoned the old botnet for a new and improved operation, running on a new strand of the Ramnit banking trojan.
IBM security experts claim that there are no huge differences between the older version of the Ramnit trojan and the newer one, except its infection method.
While the Ramnit v1 banking trojan relied on removable drives and network shares to spread to new victims, the second-generation Ramnit botnet is being built using malicious ads that redirect users to a Web page where the Angler Exploit Kit is hosted, information also confirmed by a report from Malwarefor.me from the end of November.
Ramnit is the first banking fraud botnet to resurface
These new versions of the Ramnit banking trojan work on a new C&C server infrastructure, and as IBM points out, this seems to be the first banking fraud botnet that ever resurfaces. This surprised security experts, who until now have only seen spam botnet being reborn, with cyber-crime banking fraud groups being satisfied that their botnet was taken down and they got away without being arrested.
Furthermore, IBM experts also say that, because the first Ramnit botnet has never been shared with other groups, has never had its source code leaked, or has never been a hot topic on the underground market, this second version of the banking trojan must be developed by the same people that brought out the first version, since they are the only ones that ever had access to the source code.
"At the time of this writing, Ramnit attacked major banks in Canada, Australia, the U.S. and Finland," says IBM Cybersecurity Evangelist Limor Kessem. "Judging by the previous activity of this malware, it is likely that Ramnit’s operators will spread their reach into other parts of the world in the coming months as they build their new botnet and resources."

 14 DAY TRIAL //
14 DAY TRIAL //