Tech support scammers have been taking inspiration from ransomware operators and have changed their mode of operation by creating malicious software that blocks the user's access to the computer until they contact a call center for support.
For years, tech support scams have used so-called "scareware" tactics, trying to trick users into thinking they needed technical support from an expert. These methods often used warnings and popups telling users they had malware on their computer, or a fault on their hard drive, with the computer ready to fail at any moment.
Later, the same tech support scammers developed clever JavaScript-powered tricks to lock the user into a one Web page, with the same scary messages, aiming to trick the victim into contacting their call centers.
Tech support scammers are borrowing ransomware tricks
In the latest installment of this tech support scam, the crooks have managed to find a way to lock the user's entire computer, not just their browser.
This trick is reminiscent of the early days of ransomware. Back then, ransomware didn't encrypt your files, but merely blocked access to your computer with screens overlaid over your desktop, or by disabling keyboard and mouse input.
Security researcher slipstream/RoL discovered one of these tech support scams that lock the user's entire PC. He and the team at Malwarebytes investigated this problem.
Crooks used adware to infect and lock computers
According to the two, crooks are distributing a trojan bundled as adware with legitimate programs. Once the user installs the desired software, the adware also gets installed, in the form of the trojan.
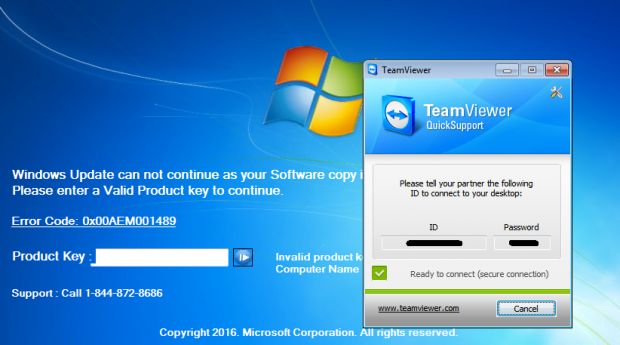
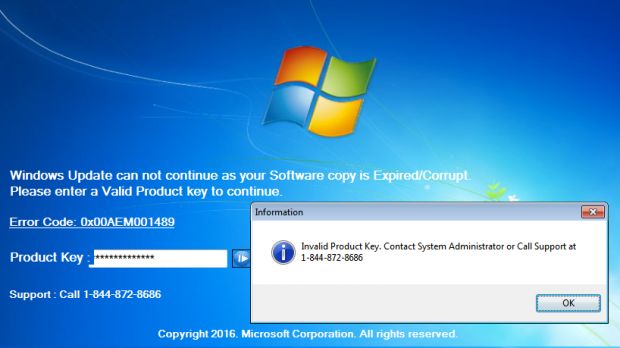
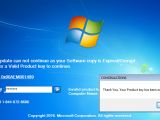
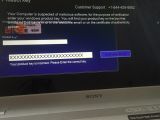
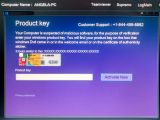
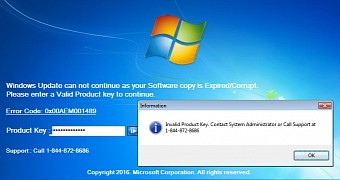
This trojan waits in hiding until the user restarts their PC. When this happens, it shows a fake Windows update screen, but when it ends, it displays a message telling the user their Windows product key expired and that users should call a phone number to speak to a Microsoft employee.
slipstream/RoL says the call center is located somewhere in India. Malwarebytes claims they've called the number, and the call center operator instructed them to press CTRL+SHIFT+T. This key combo starts a TeamViewer instance, which the call center operator will use to access the victim's computer, and presumably uninstall the trojan.
At this point, the call center operator refuses to continue the discussion until the victim makes a payment of $250.
By refusing any interaction, the tech support scammers are holding the computer and the user's data for ransom, making them a "walking & talking ransomware."
There is a way to get rid of it
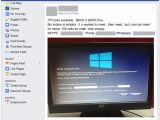
slipstream/RoL discovered that, by pressing CTRL+SHIFT+S, users can shut down the screen lock, but this doesn't give them access to the computer.
He also discovered some hardcoded serials in the trojan's source, which he says can be employed to start a Windows Explorer window that can be used to navigate the user's PC and remove the trojan. These codes are: "h7c9-7c67-jb" "g6r-qrp6-h2" "yt-mq-6w".
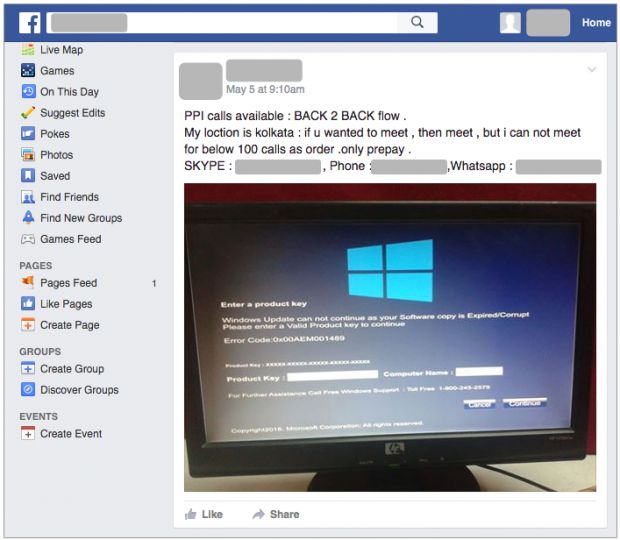
This type of tech support variation is not only novel but quite common already, and Malwarebytes has already had at least two users complain on its forum. Additionally, the researchers found this malware peddled with ads on Facebook, meaning more crooks are bound to buy it and integrate it into their tech support scams.
 14 DAY TRIAL //
14 DAY TRIAL //