Time is on the side of security researchers, who had the opportunity to take a closer look at the malware used in the Bangladesh SWIFT cyber-heist, and their conclusions are clear cut and almost unanimous.
According to reports from Symantec, BAE Systems, and Simon Choi of IssueMakersLab, the malware used in the SWIFT-based attacks closely resembles the one used by the Lazarus Group, the notorious hacker and cyber-espionage crew behind the Sony hack and multiple others on governments and private enterprises.
Malware contained a "familiar" hard disk wiping function
BAE Systems was the first one to spot the similarities two weeks ago, but security firms are known to mess up attribution once in a while. Today, when Symantec released its separate report on the malware used to infiltrate and carry out the Bangladesh $81 million cyber-heist, its conclusions were almost identical.
Both companies said the file moutc.exe contained various code functions that were near identical to the ones spotted inside malware samples deployed by the Lazarus Group in the Sony hacks.
The similarity was in the "wiping function," used by crooks to delete traces of their activity on infected systems. The Bangladesh malware (Trojan.Banswift) contained this file, which Symantec researchers quickly tied to Backdoor.Contopee, a trojan used in cyber-attacks on financial institutions in South-East Asia in the past few years alongside Backdoor.Fimlis and Backdoor.Fimlis.B.
Symantec gives its stamp of approval
Symantec had previously linked Backdoor.Contopee to Backdoor.Destover, one of Lazarus' main malware tools. If you got lost in all the complicated malware names, don't worry. The basic idea is that Symantec, one of the four main companies that helped unmask the Lazarus Group activity, said the following:
“ Symantec believes distinctive code shared between families and the fact that Backdoor.Contopee was being used in limited targeted attacks against financial institutions in the region, means these tools can be attributed to the same group. ”
Taking a closer look at the Lazarus Group report, we also see that this group, which the FBI has officially linked to North Korea, had carried out attacks against banks in 2011 and 2013, mainly in South Korea, so theoretically, the group has the arsenal to get this done.
Another SWIFT hack in the Philippines?
After new malware attacks against the SWIFT transaction system surfaced against two other banks in Ecuador and Vietnam during the past week, there are also rumors of a similar incident against a bank from the Philippines even earlier than the one carried out against the Vietnamese bank.
A US publication has gone on record and reported that US security firm FireEye is currently investigating attacks against a dozen banks from South-East Asia, with clues pointing to the same mode of operation. Furthermore, Bangladesh has also decided to reopen an older case of a suspicious bank cyber-heist from 2013, just to be sure it wasn't the same group.
It appears that after the whole media uproar surrounding the Sony hack died down, Lazarus has returned to what it does best, and that's to hack banks, at which it appears it's pretty good from the evidence that has surfaced until now.
Below is an infographic from Simon Chai of all the current details surrounding the recent attacks against SWIFT, the Web service used as a transaction system by international banks.

 14 DAY TRIAL //
14 DAY TRIAL // 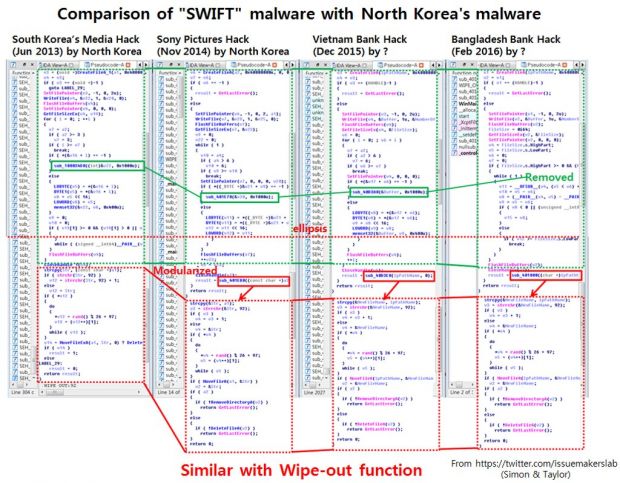
![Current status of SWIFT hacks [May 26, 2016] Current status of SWIFT hacks [May 26, 2016]](https://news-cdn.softpedia.com/images/fitted/620x/swift-bank-attacks-connected-to-north-korean-group-behind-sony-hacks-504538-2.jpg)


![Current status of SWIFT hacks [May 26, 2016]](https://news-cdn.softpedia.com/images/newsrsz/swift-bank-attacks-connected-to-north-korean-group-behind-sony-hacks-504538-2.jpg)