Hacking Team, a company that supplies surveillance programs to government agencies across the world, has been hacked, and corporate data has been leaked to the public via a torrent file weighing more than 400 gigabytes.
The cache contains emails, software source code and sensitive files such as a list of customers and the money they paid for the spying software.
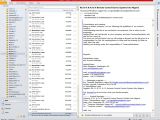
Company's Twitter profile publishes bits of leaked data
At the moment, the attackers control the company’s Twitter account, which is used to expose both internal emails and correspondence with customers. Hacking Team’s Twitter logo and short bio have been changed and now read:
“Hacked Team - Developing ineffective, easy-to-pwn offensive technology to compromise the operations of the worldwide law enforcement and intelligence communities.”
A pinned tweet on the profile says, “Since we have nothing to hide, we're publishing all our e-mails, files, and source code,” followed by links to the torrent files, thus allowing anyone with sufficient storage space to download the data.
Hacking Team is based in Milan, Italy, and it is known to develop and sell spy software for different computer platforms, both mobile and desktop, capable of evading detection of antivirus products.
In 2014, a variant of Hacking Team’s Remote Control System (RCS) went undetected by popular antivirus products like Kaspersky, Avira, G DATA and ESET.
Many govts use Hacking Team's surveillance tools
Although the fact that the surveillance products developed by the company are sold to governments, no names have ever been disclosed.
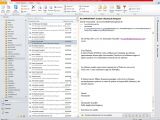
Christopher Soghoian, a privacy researcher and vocal civil liberties activist, has analyzed some of the data leaked and has found that on Hacking Team’s customer list there are South Korea, Kazakhstan, Saudi Arabia, Oman, Lebanon, Mongolia, Egypt, Ethiopia, Chile.
One of the documents included in the file dump includes a spreadsheet with every government client along with the time they first purchased services from Hacking Team and the amount they paid, Soghoian says on Twitter.
Some of the services of the company include providing zero-day exploits with the surveillance software. Apparently, such a subscription cost an additional $50,000 / €45,000 per year.
Eva Galperin, global policy analyst at the Electronic Frontier Foundation, has published a tweet with some of the customers of the company. Among the countries in Europe are Poland, Germany, Hungary, Czech Republic, Spain, Luxembourg and Switzerland.
A list with active and expired clients is also available on Pastebin; it shows the US Drug Enforcement Agency (codename KATIE) as an active client on December 31, 2014 and the FBI (codename PHOEBE) on June 30, 2015.
Needless to say that this hack exposes covert surveillance activity of governments, some of them highly oppressive, and represents a serious blow on Hacking Team's business.
Security researcher Claudio Guarnieri developed a tool for detecting traces of malware known to be used by governmental organizations for monitoring the activity of subjects of interest.
Detekt is open source and was published in partnership with Amnesty International, Digitale Gesellschaft, Electronic Frontier Foundation and Privacy International.
Congrats to the government of Chile, which in 2014 signed the largest @hackingteam contract to date: 2.85 mil USD. pic.twitter.com/MuRc6DVecl
— Christopher Soghoian (@csoghoian) July 6, 2015
Who says selling surveillance tech to govs that spy on journalists doesn't pay well? $1 mil from Ethiopia. pic.twitter.com/I3HCxdl3Gl
— Christopher Soghoian (@csoghoian) July 6, 2015

 14 DAY TRIAL //
14 DAY TRIAL //