A cyber-espionage group called Suckfly is targeting governments and big enterprises, mainly located in India, using a backdoor named Nidiran, a credential dumping tool dubbed Hacktool, Windows OLE exploit CVE-2014-6332, and stolen digital certificates.
The group first came to Symantec's attention when, in March, it was caught stealing digital certificates from various South Korean companies.
A few months later, while investigating clues left behind by the group, Symantec experts claimed to have discovered Suckfly activity going back as early as April 2014.
Suckfly group focused on Indian targets
The group mainly targeted Indian companies, but researchers found hacked businesses in Saudi Arabia as well. Symantec says it discovered the group targeted two Indian government organizations, a large e-commerce company, one of the country's biggest financial groups, one of its top five IT companies, a shipping vendor, and a US-based healthcare provider for various Indian companies.
Except one privately owned company, the group spent more time attacking the two Indian government agencies than anyone else.
"There is no evidence that Suckfly gained any benefits from attacking the government organizations, but someone else may have benefited from these attacks," Symantec's Joe DiMaggio reported. "The nature of the Suckfly attacks suggests that it is unlikely that the threat group orchestrated these attacks on their own."
Suckfly uses APT-style tactics
Symantec's analysis of Suckfly's mode of operation reveals cyber-warfare tactics employed by many APT and economic espionage groups.
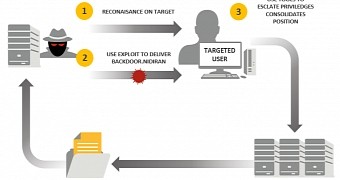
Suckfly attacks start with phishing emails that deliver boobytrapped documents. These files exploit CVE-2014-6332 to infect the target with the Nidiran backdoor, which attackers use to install Hacktool, a password dumping utility.
Crooks then use these passwords to scout and search the local network, gather any potentially interesting data and use the backdoor again to send it off to their servers.
Symantec noted that these attacks took place only on weekdays, when the group was sure to find people at work to read the spear-phishing emails.
At the moment, security researchers could not exactly tell if the group is state-sponsored or not.
 14 DAY TRIAL //
14 DAY TRIAL //