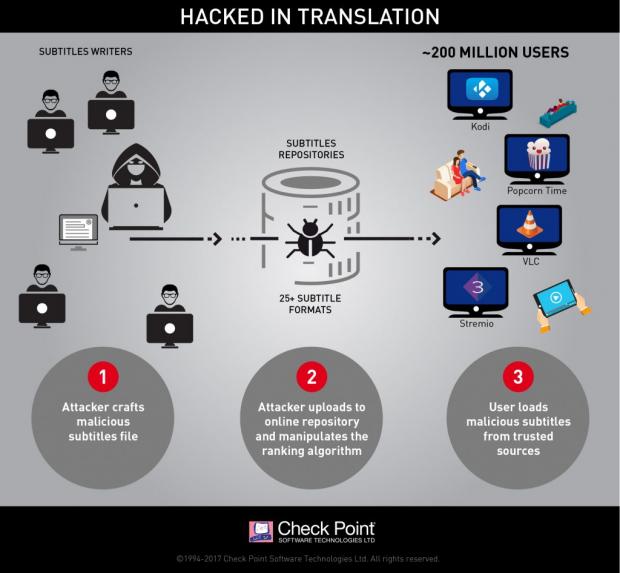
About 200 million users of video players and streamers are vulnerable to an attack that uses malicious subtitle files.
According to security researchers from Check Point, the attackers can execute remote code on PCs, Smart TVs, and mobile devices using popular video players and services such as VLC Media Player, Kodi, Popcorn Time, and Stremio.
"This is a brand new attack vector. We haven't seen this type of attack yet in the wild. But we believe there are upwards of 200 million video players and streamers vulnerable to this type of attack," writes Omri Herscovici, team leader for product research and development.
It seems that each media player the company has looked at has a unique vulnerability that allows a remote attacker to execute code and gain control of the targeted system after the malicious subtitle file has been downloaded. While refraining to offer too many details on the way they managed to test this exploit, the researchers did mention that they took advantage of a memory corruption vulnerability in VLC in order to gain control of the PC.
The only reason VLC was singled out is because they've been made aware of four separate vulnerabilities back in April and they've all been patched already. Therefore, if your favorite player is VLC, make sure you've updated to the latest version.
A great risk
In the proof of concept attack, security researchers from Check Point say that victims were pushed to visit a malicious website that uses one of the streaming video players, or they were tricked into opening a malicious subtitle file on their system, which they downloaded to use with a video.
"By conducting attacks through subtitles, hackers can take complete control over any device running them. From this point on, the attacker can do whatever he wants with the victim’s machine, whether it is a PC, a smart TV, or a mobile device. The potential damage the attacker can inflict is endless, ranging anywhere from stealing sensitive information, installing ransomware, mass Denial of Service attacks, and much more," reads the research.
The heart of the problem is the bad coding of subtitle parsing implementation. There are dozens of subtitle formats and no standards for parsing. "Each one of the players we looked at uses a homegrown version of a subtitle parsing implementation. And each of them had a remote code execution flaw," mentions Herscovici.
In order for the exploit to work, the malicious subtitle file must be selected to run with the video. Another scenario sees a victim playing a video that is pre-programmed to download a subtitle file from an online repository. According to the researchers, sites such as OpenSubtitles.org, which is also used by software such as BS Player, is the perfect place for a potential attacker to dump infected files.
 14 DAY TRIAL //
14 DAY TRIAL //