Login credentials for 47 government agencies in the United States have been stolen and dumped online between November 2013 and November 2014, following data breaches.
The sensitive information belonged to 89 unique domains and was discovered in publicly available locations such as Pastebin by Recorded Future, a data analysis company that gathers open source intelligence (OSINT).
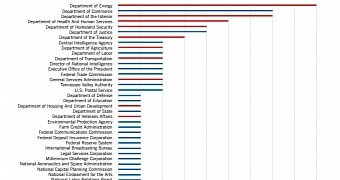
In early 2015, 12 agencies still lacked 2FA protection
In a report published on Wednesday, company researchers said that the information was collected from 17 paste sites and that it had been shared with the affected agencies in late 2014 and early 2015.
It is not clear how cybercriminals managed to obtain the information, but lack of the two-factor authentication (2FA) security measure may have played an important part. “As of early 2015, 12 of these agencies allowed some of their users access to computer networks with no form of two-factor authentication,” the report says.
During the analysis, Recorded Future discovered that email addresses and their corresponding passwords for 9 domains of the Department of Energy were available online, with the Department of Commerce coming in second with exposures for 7 of its domains.
Attacks were not always targeted
The leaks were not always a result of targeted attacks, such as those from hacktivist groups, and many of the credentials were included in dumps related to hacks carried out by exploiting vulnerable third-party sites, services, or individuals.
In a recent report from Veracode, it is revealed that applications used by government agencies benefit from minimum attention as far as security vulnerabilities are concerned, compared to problem remediation practices in other sectors.
“The presence of these credentials on the open Web leaves these agencies vulnerable to espionage, socially engineered attacks, and tailored spear-phishing attacks against their workforce. While some agencies employ VPNs, two-factor authentication, and other tokens to provide a safety net,” the report states.
Determining the date of an attack or whether the sensitive information was used for further network infiltration activities cannot be established, given that the data was dumped publicly by the hackers without providing any context.
 14 DAY TRIAL //
14 DAY TRIAL //