A cyber-espionage group codenamed Stealth Falcon is using a combination of home-cooked malware and social engineering tactics to spy on Emirati journalists, activists, and dissidents, The Citizen Lab team at the University of Toronto reported this weekend.
The United Arab Emirates (UAE) has been one of the Hacking Team's most loyal customers, using its spyware and surveillance software to target and monitor its own citizens, with at least three high-profile cases making it into international media.
But as the Hacking Team's activities were exposed last summer, the company lost a lot of its customers, who either moved to other government surveillance suppliers such as Finfisher, NSO Group, and Cellebrite, or started developing their own monitoring software.
Stealth Falcon APT campaign leveraged Twitter and shortened URLs
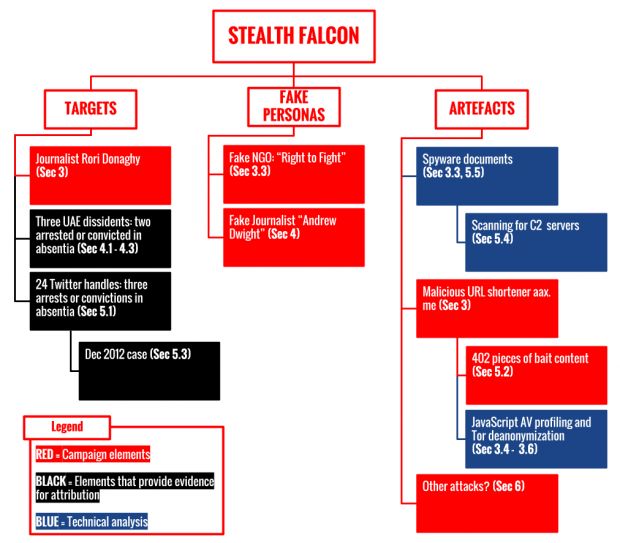
The Citizen Lab team revealed in its latest report that UAE seems to have moved on from Hacking Team's RCS surveillance kit, and is now using custom spyware developed by an advanced persistent threat (APT) group called Stealth Falcon, whose activities left a trail of breadcrumbs back to the UAE government.
In its most recent wave of attacks, the group has used spam email and social media messages, usually spread via Twitter, to infect victims. Both delivery methods used a series of subjects and themes that were critical of the UAE government, aimed at people known to show such behavior.
The social media Twitter campaign was aimed at 27 targets, with 31 tweets containing links that redirected users through a URL shortening service (aax[.]me).
Victims got infected with spyware after enabling macro support in Office docs
Citizen Lab researchers said this URL shortening service was fingerprinting users to get a better understanding of the software they were using, and then they were redirecting users to their final destination.
Researchers brute-forced all the possible short URLs on that service and discovered 402 links leading to bait content, 73 percent of which referenced various UAE-related issues.
Stealth Falcon also employed a similar campaign using emails instead of tweets, using the same shortened URLs. While in some cases the shortened URLs only profiled users and redirected them to their destination, there were cases where the users received spyware at the end of these links.
Additionally, the group also sent Office documents as email attachments. The users were asked to enable macros inside their Office installation to view the document. In reality, this would infect their computer with spyware.
Citizen Lab researchers say that these spyware infections would then collect data from each victim and send it to at least 67 C&C (command and control) servers.
Some of the targets ended up in arrested, some were even convicted
Citizen Lab researchers say they managed to discover the real person behind the 27 Twitter accounts targeted by Stealth Falcon. Of these, UAE authorities arrested five and convicted two.
"Circumstantial evidence suggests a link between Stealth Falcon and the UAE government," the Citizen Lab team noted. "While there is no 'smoking gun,' several pieces of evidence suggest a connection between Stealth Falcon and the UAE Government."
This "smoking gun" evidence refers to the fact that almost everyone targeted in these campaigns has had run-ins with Emirati police, and that a government account once tweeted out one of the shortened URLs. Furthermore, the fact that the group had some familiarity with the interests and activities of its targets, which only a state-sponsored group would be able to attain, also points out to some sort of connection to UAE government entities.

 14 DAY TRIAL //
14 DAY TRIAL //