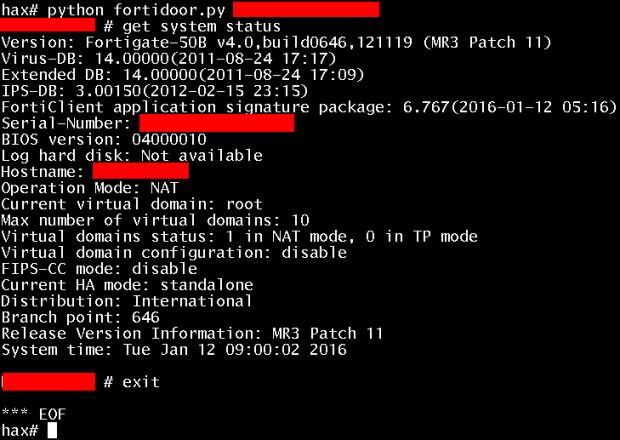
Fortinet's FortiOS operating system, deployed on the company's FortiGate firewall networking equipment, includes an SSH backdoor on versions from the 4.x series up to and including 4.3.16, and the 5.x series up to and including version 5.0.7.
This vulnerability is not a deja vu of the Juniper incident and seems to be a completely different issue, having nothing in common with the backdoor identified in Juniper's ScreenOS.
FortiOS SSH backdoor can be accessed via the Fortimanager_Access username
Discovered by a user who wanted to remain anonymous ([email protected]), this flaw exposes a backdoor to Fortinet firewall equipment that can be accessed via SSH connections.
While there's a low chance that any professional sysadmin would expose their SSH port to the Internet, this backdoor can still be exploited if an attacker gains access to the local network or a virtual LAN by infecting an organization's PC.
If this happens, the attacker can access a Fortinet network security equipment by logging in using the "Fortimanager_Access" username and a hashed version of the "FGTAbc11*xy+Qqz27" string as password. This user may be tied to Fortinet's FortiManager product, advertised by the company as "an easy to use, centralized, 'single pane of glass' management console."
As Rik van Duijn noticed, "the FortiGate backdoor gives a variable that is then used to create a base64 string for authentication."
Another explanation for the username/password combo was provided by Evan Anderson: "It's a custom SSH authentication method invoked with a special username, 'Fortimanager_Access.' The protocol is a weak 'challenge/response' using hash of the challenge concatenated with a string (used in multiple firmware versions and not at all unique to the device)."
Proof-of-concept code is available for wannabe hackers
Proof-of-concept code to generate the backdoor's dynamic password is available. Sysadmins can also use this code to automate the testing process and see if they have any vulnerable FortiGuard equipment laying around.
While the initial report was vague, the infosec community on Reddit and Hacker News has managed to narrow down affected FortiOS versions to the 4.x branch up to 4.3.16, and the 5.x branch up to 5.0.7.
The SSH backdoor is not present on any of Fortinet's more recent versions of the FortiOS operating system.
Backdoor logins are not logged by the device
A Reddit user noticed that there might be a connection between the backdoor's disappearance and a critical security bug (CVE-2014-2216) that Fortinet fixed back in 2014 (confirmed, see below).
The same Reddit user also discovered that anyone using this backdoor account does not appear in the device's access logs. This seems to confirm that the backdoor might be tied to the FortiManager maintenance platform.
"It keeps working even if you disable 'FMG-Access,'" he said after trying to disable the user/FortiManager (still not clear which one he meant). "It won't let you define an admin user with the same name to mitigate it, so make sure that SSH access on your devices is at least restricted to trusted hosts."
We have reached out to Fortinet for more details, and we'll update the article if they become available.
UPDATE: The company has published a statement on its blog regarding the incident. In short, it goes like this: "This was not a 'backdoor' vulnerability issue but rather a management authentication issue. The issue was identified by our Product Security team as part of their regular review and testing efforts."

 14 DAY TRIAL //
14 DAY TRIAL //