One careless employee is all it takes to take down a company, as a recent incident report from the Exploratorium Museum reveals.
The incident in question took place on September 6, when an employee of the Museum of Science, Art, and Human Perception in San Francisco, also known as the Exploratorium, fell for a well-crafted spear-phishing email.
Early in the morning of September 6, an Exploratorium employee received an email from a mailing list she had subscribed to, which contained a link to a document shared among the mailing list's members.
When she accessed the link, the employee was welcomed by the familiar Google login screen, where she carelessly entered her credentials, without checking the URL. In reality, the employee had just sent her Gmail's account credentials on a phishing page, which sent them to a hacker overseas.
Attacker studied the hacked account for three days
As the Exploratorium Museum's IT staff explain, the hacker lay dormant for three days, during which he read the employee's email and studied her contact list.
On September 9, the attacker sprung into action. He logged into the employee's Gmail account and executed three operations.
First and foremost, the attacker deleted her contact list. Secondly, he redirected all incoming emails to the trash folder, and third and last, he sent out other spear-phishing emails to all her colleagues, based on what he thought her colleagues would normally expect to receive from the employee.
Grammar mistakes in spear-phishing emails strike again!!!
Despite this, Exploratorium's staff detected something suspicious about the email, which tried to lure users to a phony Google login page, with the promise of accessing a document titled "Explratorium Report." The problem was the Museum's mispelled name, an error a museum employee would never make, especially in a report.
If scammers really want to fool people with phishing emails, maybe they should learn to spell first? Proper grammar wouldn't go amiss either — Brian Healy (@Brian_Healy) August 3, 2012This is where those first two steps the attacker took came in handy. All the emails from friends asking the employee if she got hacked were redirected to the Trash folder. The employee was only alerted to the incident later on after someone came to her desk and told her what happened.
When the employee wanted to warn her friends not to open her previous email, she discovered that her address book had been deleted.
Attackers were from Nigeria
Fortunately, by this time, the Museum's IT staff had been alerted and stepped in to mitigate the attack by sending a company-wide alert, and resetting the employee's Gmail password.
Unfortunately, the harm had already been done, as some workers fell victims to the employee's email, and had entered their Gmail credentials on the phishing page.
"Throughout the next several weeks our email accounts were being periodically probed for password weaknesses," the Exploratorium IT staff explains. "These alerts had a chilling quality to them, a bit a like if you changed the locks on your house and then received a note every time someone tried to break in with the old key."
IT staff said that 54 employees had clicked on the phishing email, but it's uncertain how many had entered their credentials.
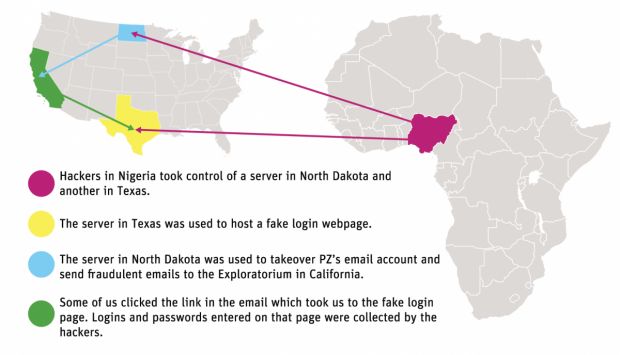
A subsequent investigation using the forensic tools from Google Apps revealed that the attackers were based in Nigeria, and had rented a server in North Dakota from where they accessed the employee's Gmail account, and another server in Texas, where they hosted the phishing pages.

 14 DAY TRIAL //
14 DAY TRIAL //