Malware keeps getting more and more clever, and a trick that's worth mentioning is one discovered by the researchers at Palo Alto's Unit42 research team, who recently uncovered a spambot that checks if the infected victim's IP is included in a spam blacklist before using the PC to send out unwanted emails.
The tactic is clever and devilish at the same time and shows why fighting spam is a 24/7 job, not just a one-time duty.
The malware in question is named Sarvdap, a generic term given by Microsoft to a broad set of malware variants used for transforming regular PCs into spambots.
Sarvdap part of the Andromeda botnet
Palo Alto says it detected this Sarvdap variant distributed by the group behind the ancient Andromeda botnet, and they used it to spread pharma spam and the Andromeda malware itself, in order to keep the botnet going.
An analysis of the malware revealed a series of tricks not seen in similar spambots.
After infecting the host, Sarvdap makes a place for itself in the user's %windir% folder, starts its own svchost.exe (Windows service host) process, and checks for an Internet connection by trying to access microsoft.com.
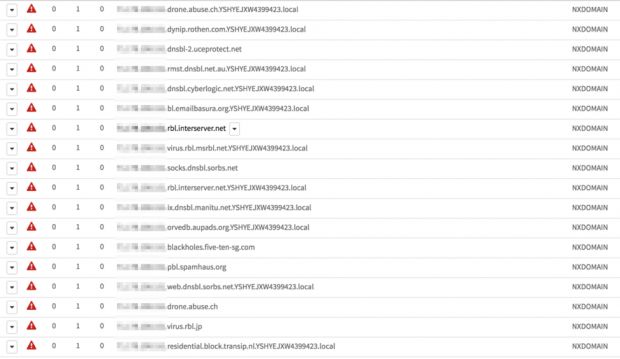
Sarvdap checks the user's IP address against several RBLs
If the user is connected to the Internet, Sarvdap will determine the local computer's external IP address and query various spam blacklist services, also called RBLs or Reputation BlackLists.
RBLs are dynamic lists of IP addresses from where the world's spam originates. Various Internet security services maintain their own RBL, and email providers and firewall vendors use one or multiple RBLs to block malicious traffic.
If queries to these RBL APIs return a negative result, the spambot terminates immediately. If the queries return a positive result, Sarvdap will continue its malicious behavior by contacting a command and control server and asking for a configuration file.
Because the C&C server was down at the time of their analysis, Palo Alto researchers weren't able to determine other details included in the configuration file besides the content of the spam emails and the targeted email addresses.
Stopping little spambots like Sarvdap might seem less important than stopping banking trojans and rootkits, but it's these smaller threats that help spread the latter.

 14 DAY TRIAL //
14 DAY TRIAL //