A scheme that involved bribes, mobile apps, steganography, and a distraught antivirus maker allowed crooks to steal login credentials from Chinese merchants.
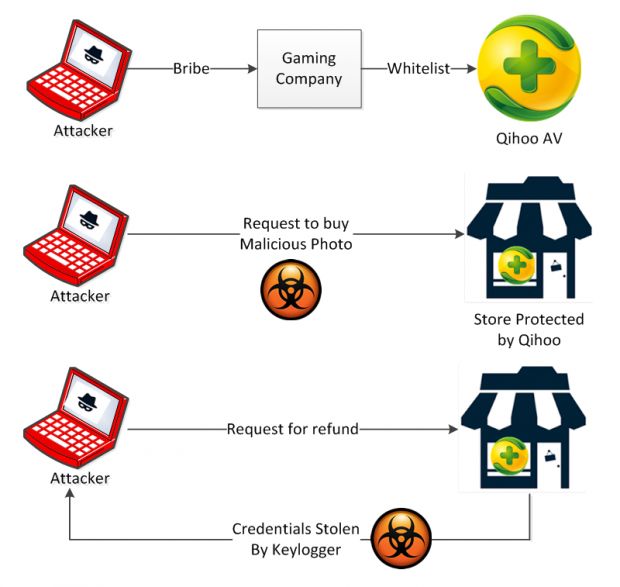
Malware operators utilized this particular attack scenario in China, where they bribed the employees of an authorized gaming company in order to embed samples of their malware in the source code of one of their many mobile apps.
Crooks bribed gaming company employees
The gaming company used its influence and past history to appeal to Qihoo 360, China's biggest antivirus maker, to whitelist the apps, in order for Chinese users to be able to install them from third-party app stores without prompting them with malware warnings.
According to security firm Check Point, Qihoo 360 appears to have trusted the mobile apps received from the gaming company and whitelisted them in its products without a thorough inspection.
But this was not a classic malware attack in any way or form. Instead of activating the malware on devices where the gaming apps were installed, crooks used a different scheme, which involved the Taobao.com marketplace, China's eBay clone.
If you're non-Chinese, some extra details are needed beforehand. Taobao doesn't work exactly as eBay does, but instead of direct payments, it uses the Aliwanwang instant messaging application to allow users to send a picture of the product they want to buy to the store owner.
The store owner validates the purchase and requests payment via Alipay, Aliwanwang’s payment platform.
Crooks hid keyloggers in images
The crooks were taking pictures of products from legitimate stores, embedding their malware using steganography techniques right inside the image, and sending the malicious photo to the store owners, going through with the purchase.
The image would reach the store owner, and the malware would escape the image when viewed by the merchant, installing on their device and starting a keylogging feature. Because the malware was part of the whitelisted apps, Qihoo's antivirus wasn't raising any alarms regarding the images or the keylogger.
Later on, the attacker would request a refund, which meant the store owner would have to authenticate on Alipay to reverse the transaction.
The crook's malware would record these credentials and send them back to the attackers, who would later hijack the store owner's account, stealing their funds.

 14 DAY TRIAL //
14 DAY TRIAL //