Some basic security principles and best practices are being ignored in Germany and other European countries, a recent Security Research Labs investigation reveals.
Experts from Security Research Labs claim that most payment terminals used in Germany implement older protocols, known to be vulnerable, but also use bad practices when it comes to data encryption.
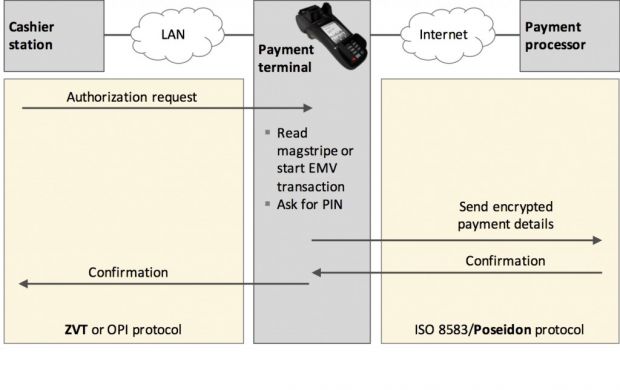
According to the researchers, the problem relies on both sides of the barricades, with the protocol used to talk between the cashier station and the PoS, and the protocol that sends data from the payment terminal to the payment processor/bank.
Vulnerable on the inside...
On the local side, researchers found that a high percentage of German payment processors use the ZVT protocol, known to be susceptible to simple sniffing attacks that allow attackers to intercept data about credit cards.
What makes things worse is that this protocol is also responsible for reading the card's PIN via the PoS and sending the appropriate acknowledgements back to the cashier to allow the transaction.
While this is all done using encryption, researchers found that PoS makers store the encryption key on the device, and often reuse the same key for entire batches.
If attackers can compromise one PoS terminal and extract the encryption key, they'll then be able to read encrypted traffic exchanged via a store's local LAN network, and read card numbers, along with their associated PINs.
... vulnerable on the outside
Between the PoS terminal and the payment processor/bank, things aren't that rosy either. The protocol used for exchanging data between the two, a variant of the ISO 8583, known as Poseidon in Germany and other countries, features an authentication flaw.
Repeating the same mistake, PoS makers also store the encryption key used for exchanging encrypted data with outside parties. This key is stored on the device itself and is rarely changed, being most of the times the same for entire batches of PoS terminals.
"Fraudsters can, among other things, refund money, or print SIM card top-up vouchers - all at the cost of the victim merchant," say Security Research Labs experts about the dangers of keeping the Poseidon encryption key on multiple payment devices.
The researchers are planned to give an expanded presentation on this topic December 27 in Hamburg at the 32nd Chaos Communication Congress (32C3).

 14 DAY TRIAL //
14 DAY TRIAL //