The Sofacy cyber-espionage group, also known as Fancy Bear, APT28, Sednit, Pawn Storm, or Strontium, has developed new hacking tools, which they've deployed over the summer in live attacks.
According to Palo Alto Networks, the group targeted a Ukrainian defense organization and the Minister of Foreign Affairs of a nearby country.
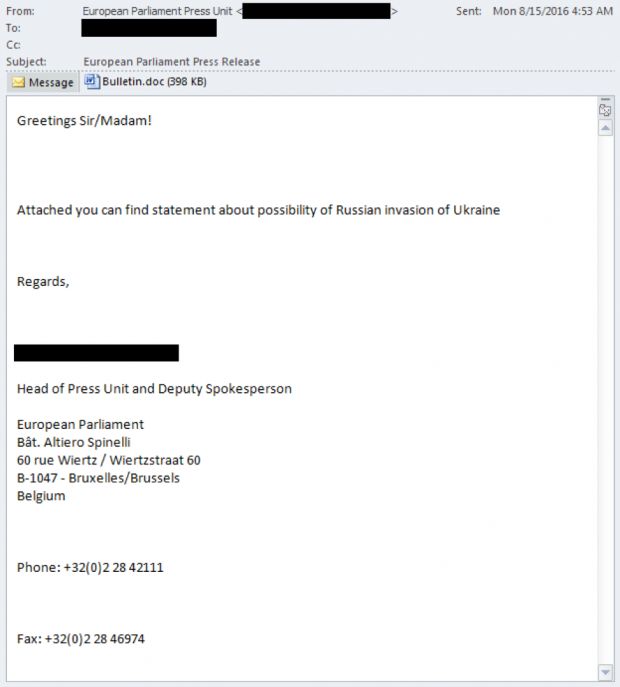
Sofacy used spear-phishing emails to deliver malicious documents to their victims. The group spoofed communications from the European Parliament’s Press Unit in order to fool recipients.
Flash exploits hidden in multi-layered Office files
The spear-phishing campaign delivered malicious documents about a possible Russian invasion of the Ukraine, drawing the recipient's attention.
According to Palo Alto, when a victim would open these documents, they'd be presented with decoy files instead, which contained text copy-pasted from international news media. Under the hood, the original files would load another Word document via embedded OLE objects, which would, in turn, contain Adobe Flash SWF files.
These double-nested Office files would attempt to exploit the user's PC for unpatched Flash vulnerabilities.
Sofacy develops new Flash exploitation framework
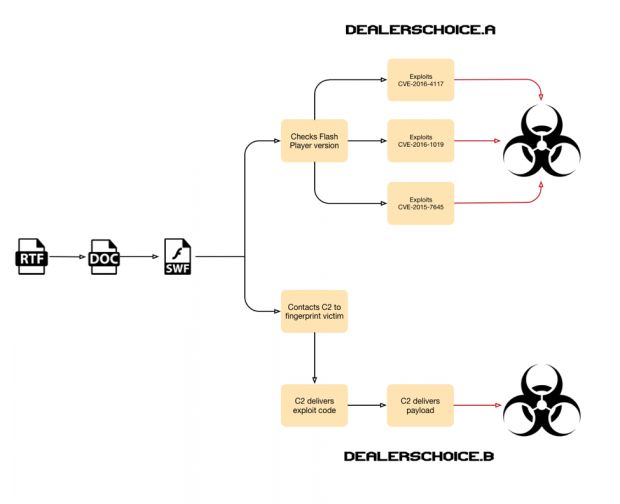
Researchers said they identified two distinct sets of attacks using these tactics, deploying two different variants of the embedded Flash SWF files, which they named DealersChoice.
Attackers deployed both versions, DealersChoice.A and DealersChoice.B, within weeks of one another in the month of August.
The differences between the two are significant. DealersChoice.A is a self-contained exploit package, while DealersChoice.B was a modular system that communicated with an online command and control server.
For DealersChoice.A, the malware analyzed the local system for the current Flash version and delivered one of the payloads contained within. For DealersChoice.B, the initial module scanned the system and informed the server, which, in turn, sent only the appropriate exploitation package to the victim's PC.
DealersChoice used Flash vulnerabilities such as CVE-2016-4117, CVE-2016-1019, and CVE-2015-7645.
Security experts suspect that DealersChoice is the product of a new exploitation framework put together by the Sofacy group. It is unknown if the two variants are two separate tools, or DealersChoice.B evolved from DealersChoice.A.
Infrastructure tied to previous Sofacy attacks
According to Palo Alto researchers, the infrastructure from which these emails were sent, and where the C&C server was hosted, had ties to previous Sofacy attacks, with the threat group using the same email address to register domains for these attacks, but also previous campaigns.
"DealersChoice is an exploit platform that allows the Sofacy threat group to exploit vulnerabilities in Adobe Flash. Cross-platform exploits are obviously a focus for Sofacy, as they included checks within DealersChoice to determine the operating system of the targeted system," Palo Alto researchers say.
"These checks were specifically for Apple’s OS X operating system, which coupled with our discovery of Sofacy’s Komplex OSX Trojan suggests that this threat group is capable of operating in both Windows and Apple environments," the security firm also added.
 14 DAY TRIAL //
14 DAY TRIAL //