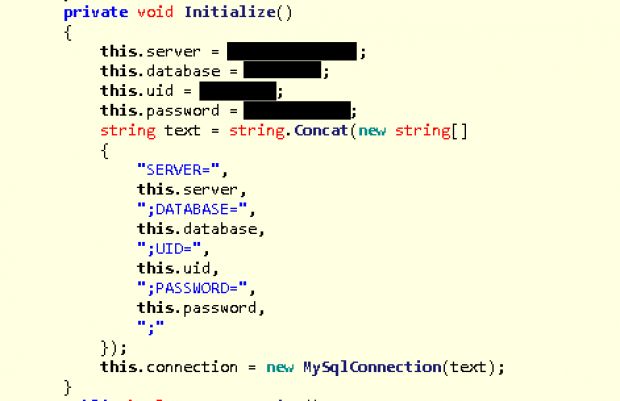
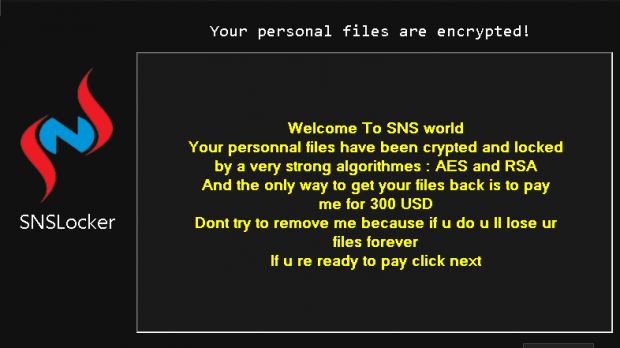
Epic fails happen all the time, but in the world of infosec, there are very few that can top this one. As Trend Micro has reported today, the author of the SNSLocker ransomware forgot the access credentials to his C&C (command and control) server in the ransomware's code.
The credentials provided Trend Micro researchers with full access to his master server, where they were able to recover the private encryption keys needed to unlock the files of all users infected with this ransomware variant.
While initially the mistake took researchers by surprise, in the end, they realized they were dealing with a less skilled malware coder, who didn't ever bother buying a VPS (Virtual Private Server), but kept his C&C server on a shared hosting provider, where it was susceptible to easy takedown requests.
SNSLocker appeared towards the end of May, and Trend Micro says it closely followed the pattern of all modern-day crypto-ransomware families.
There's the same dual AES-RSA encryption model, the classical lockscreen threat, the ransom note timer, and even the same ransom amount, with SNSLocker requesting $300, which is about the average payment demand.
The ransomware is coded in the .NET Framework 2.0 framework, and researchers say it managed to infect users all over the world, with a third of its victims in the US.
All clues point to a new ransomware actor who's just entering the market, and he may have just botched his entry.
 14 DAY TRIAL //
14 DAY TRIAL //