One month later, the SlemBunk Android banking trojan is still going strong, FireEye researchers confirming that despite its activities being made public, the malware's operators have continued to infect users and steal their financial information.
SlemBunk, first discovered by FortiNet last year, has intensified its activities towards the middle of December 2015 when FireEye researchers saw a spike in activity.
The banking trojan managed to infect users all over the world, targeting 33 mobile banking applications via 170 different SlemBunk variants.
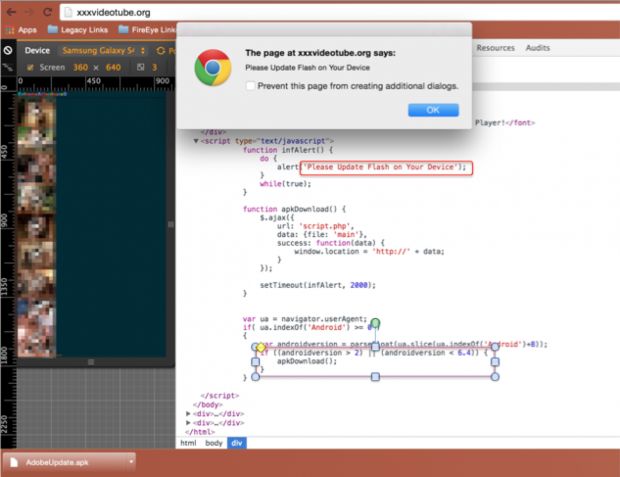
For most of these infections, SlemBunk was offered to its victims as an Android version of the Adobe Flash Player on adult-themed video portals where access to videos was blocked because users didn't have their "Flash Player up to date."
According to FireEye, this campaign has suffered very little modifications after they dissected the SlemBunk's malware mode of operation.
SlemBunk campaign carried on unabated
Following through on their previous work, security researchers continued to monitor SlemBunk infections and discovered that before the banking trojan lands on the users' devices, up to three intermediary apps are used to mask the final infection.
This prolonged attack chain usually starts with a drive-by download attack that automatically starts a download for the SlemBunk dropper (dropper - malware that serves to initially penetrate systems), which unpacks another app that serves as the SlemBunk downloader (downloader - malware that downloads other malware), which in turn downloads the final SlemBunk payload (the actual banking trojan).
Additionally, besides the fake Flash Player app, FireEye researchers also identified SlemBunk posing as other types of apps as well, from essential tools to adult-themed apps, and all distributed from sources outside the Play store.
The researchers identified the campaigns' CnC server, even reaching its login page. Most of these domains were registered at the start of December 2015, but their operators already abandoned them and moved to new ones. As it stands now, SlemBunk's operators don't seem to look scared or threatened by the security firm's discoveries, being always one step ahead.

 14 DAY TRIAL //
14 DAY TRIAL //