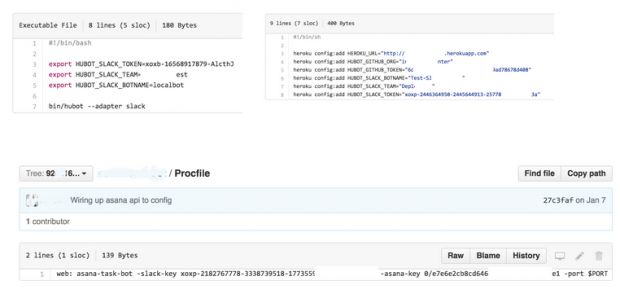
Careless developers from companies around the world have forgotten to remove sensitive API access tokens from Slack bots uploaded on GitHub, security researchers from Detectify Labs reported today.
Security experts claim they've found over 1,500 Slack access tokens while scanning GitHub projects. Most of these tokens have been found in Slack bots, small apps that allow developers to automate various operations inside Slack channels.
Slack is one of today's most successful Silicon Valley companies, enabling users to create private or public chat rooms, on demand, to use for personal purposes or for their businesses.
Slack chat rooms have become the de-facto method of communication in many companies, providing a serious competition for XMPP-based chat clients.
No API access token should be made public
According to Detectify researchers, companies may be at risk because of this bad habit their developers exhibit by leaving sensitive credentials inside open-sourced code.
The same API access tokens that grant bots the access to the organization's Slack channel, and inherent resources, can also give an attacker access to those items as well.
A malicious actor could use a Slack API access token found on GitHub to download a Slack channel's chat history and search for sensitive information like FTP credentials, internal URLs, or other types of passwords.
Researchers said the access tokens they've discovered belonged to Forbes 500 companies, payment providers, multiple internet service providers and health care providers.
Slack revoked all the carelessly shared API tokens
According to Slack's official documentation, the access tokens would have allowed attackers to access APIs for harvesting user data, Slack channel conversations and files, group information, private messages, and automate the use of Slack's search feature.
Detectify notified Slack of all the 1,500 API access tokens it discovered, and the company moved to have them all revoked while also informing all customers of the issue.
"GitHub is full of sensitive data," researchers concluded. "Slack just made it really simple to search for their tokens due to how they are formed. We hope that this advisory might help people realize how big impact getting these tokens exposed really is."

 14 DAY TRIAL //
14 DAY TRIAL //