Portuguese Web security researcher David Sopas has uncovered an RFD (Reflected File Download) vulnerability on Shopify's platform, which, according to his vulnerability disclosure, the company refused to patched.
An RFD (Reflected File Download) attack relies on hackers crafting URLs which when clicked by their victims open a file download that seems to be coming from a trusted domain.
Because the source of this kind of downloadable files can be sites like Google, Microsoft, Twitter, and so on, users generally tend to click them and execute the malicious payload without even thinking twice about it.
One such vulnerability was found on Shopify, an online platform which allows users to easily set up online shops using a visual interface, and then have them hosted on Shopify's cloud infrastructure.
According to the research carried out by Mr. Sopas, the app.shopify.com domain is susceptible to a Reflected File Download attack which would allow hackers to trick users into downloading dangerous files onto their computers.
The RFD attack is exploitable via old and new browsers alike
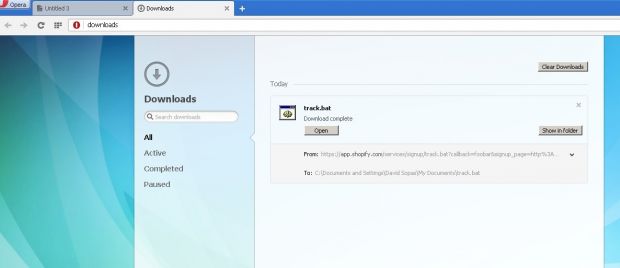
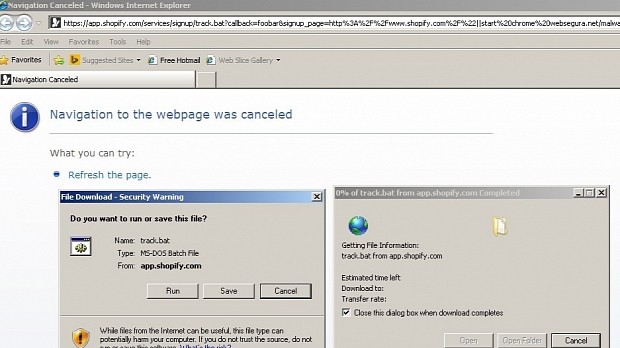
In Internet Explorer 8 and 9, Mr. Sopas claims that by accessing a malformed link, users will be faced with the option of downloading a simple .bat file.
While in his example the .bat file only opened a Chrome browser instance and redirected the user to a Web page showing some raw text, he says that attackers won't be so unimaginative and would use this vulnerability to execute more dangerous code, which would grant them access to the user's PC, in case they don't just redirect them to a Web page serving an exploit kit.
The RFD vulnerability is also exploitable via newer browsers, not just old IE versions, but the file needs to be declared via a "download" attribute inside a linkable element on the page, and not integrated in the malicious URL like in IE.
When the user eventually clicks the malformed link, he is greeted by the same download confirmation popup, with the file's location being from Shopify.
"In my opinion this was the last time I’ll send anything to Shopify," noted Mr. Sopas after being told "that their prioritization is not up for discussion and [Shopify is] not patching any time soon."
The vulnerability was discovered on March 19, 2015, and is still unpatched. This will probably change after the InfoSec media covers this story for a few days.
 14 DAY TRIAL //
14 DAY TRIAL //