On Saturday, September 24, the Shellshock bug turned two, but threat actors haven't forgotten about it just yet, with a fairly decent amount of Shellshock scans taking place on a regular basis, according to telemetry data gathered by IBM X-Force.
Shellshock (CVE-2014-6271), which is a severe security flaw in GNU Bourne Again Shell (Bash), was disclosed on September 24, 2014, and researchers said it affected all Bash versions released in the past 20 years, touching all UNIX systems that deployed it.
The open source community supplied a patch almost immediately, but that didn't mean servers owners rushed to apply it. As soon as the vulnerability became public, IBM says it detected 2,000 security incidents related to the bug.
Shellshock scans rose above a few hundred thousand in the following months, with bad actors looking for a way into unprotected UNIX machines.
The presence of a public exploit and the incredible simplicity with which someone could use it meant that any bored script kiddie could yield a Shellshock scanner, trying to compromise as many servers as possible.
Shellshock bug still going strong on its two-year anniversary
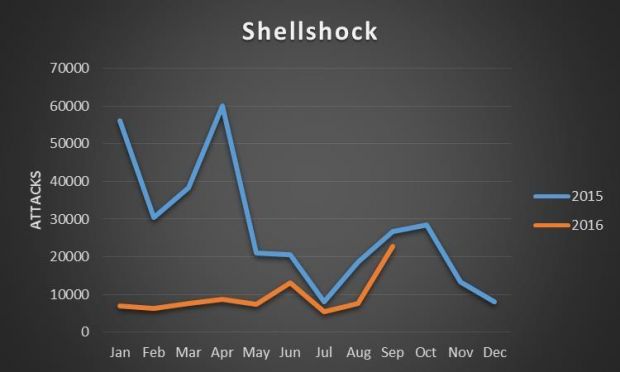
As time went by, the number of scans diminished, but according to IBM, not fast enough. Currently, Shellshock scan levels are almost at last year's numbers, which is extremely surprising for a two-year-old bug.
While scans for the four-year-old Heartbleed vulnerability are now in the range of hundreds per month, Shellshock scans have remained above 10,000 per month, with over 20,000 detected just for the month of September 2016.
IBM says most of this scans target US companies (46 percent), but this was to be expected since most of today's business world is concentrated in North America.
What is surprising is that the financial sector is not the most targeted vertical. Over 46 percent of all Shellshock scans target companies in the information and communication sector, while the financial sector is the target of 26 percent of all scans, most likely because most financial institutions have made sure to protect and upgrade their systems.
While vulnerable systems will always remain online, the high number of Shellshock scans also means that threat actors are finding, even today, unpatched systems, and that's why they continue to scan in such massive numbers, knowing they'll hit jackpot.
 14 DAY TRIAL //
14 DAY TRIAL //