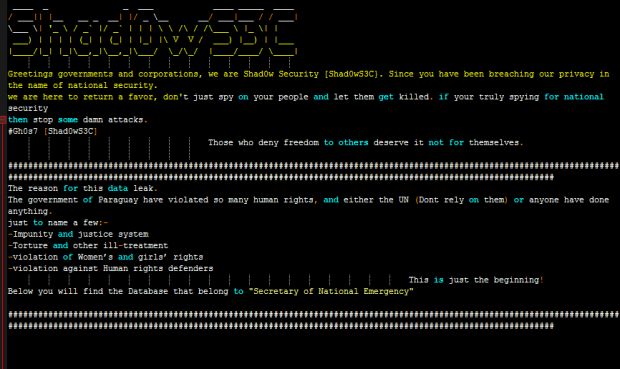
Shad0wS3C, a new hacking group formed two months ago, has made its presence felt on the hacking scene by leaking data from Paraguay's Secretary of National Emergency (SNE).
The data, of which Softpedia received a copy for the purpose of reporting on the incident, appears to be a basic dump from a PostgreSQL database.
Softpedia was alerted to the incident by Gh0s7, Shad0wS3C's leader and founder. Softpedia received the data last week, and during this time, the sen.gov.py has been operational at all times.
Softpedia has reached out to Paraguay's Secretary of National Emergency in an attempt to inform them of the leak so that the institution can investigate and plug any server holes. We have not received an answer in time for the article's publication.
Leaked data contains minimal PII
A quick analysis of the leaked data reveals information about material stocks, billing data, activity logs, but also user records from SNE employees.
SNE employee personally identifiable information (PII) includes details such as names, phone numbers, emails, addresses, salary information, and more. Basically, all the contact details and roles for each employee, in the case of national emergencies.
The dumped data also contained details on 412 website user accounts, complete with hashed passwords (keys).
Shad0wS3c - a new hacktivism group
Shad0wS3c, who formed at the start of July, had the following to say regarding the reasons behind leaking the data to the public.
The government of Paraguay have violated so many human rights, and either the UN (Dont rely on them) or anyone have done anything. just to name a few:
-Impunity and justice system
-Torture and other ill-treatment
-violation of Women’s and girls’ rights
-violation against Human rights defenders
The SNE data dump is actually Shad0wS3c's second hack. Before this, the group leaked the EJBCA database of EveryWare, a Swiss-based Certificate Authority (CAs). EJBCA is a free software package that CAs use to manage public key infrastructure (PKI).
Softpedia received a copy of the data as well but did not run a story because it could not verify if the leaked data contained active VPN keys, as Shad0wS3c had claimed.
Below is a screenshot of the dumped data. A link to the leaked SNE and EveryWare databases are still currently available on Twitter.

 14 DAY TRIAL //
14 DAY TRIAL //