In a surprising turn of events, Check Point security researchers managed to breach and then take over a phishing server belonging to Rocket Kitten, a group of hackers linked to the Iranian government.
Rocket Kitten is a hacking group that first appeared in April 2014 and was unmasked for the first time by FireEye researchers in May 2014. The most damning report on their activity was published this year by a joint effort between Trend Micro & ClearSky.
Since their first appearance, the group's main targets were individuals and institutions that opposed or criticized the Iranian government.
As both the original Trend Micro & ClearSky report and the latest Check Point findings show, the group's MO included launching spear-phishing campaigns against its targets, using social engineering tactics, and then infecting the victims' computers with malware.
Their tactics never evolved past this point, but only made small tweaks to their operations' code to avoid detection by security tools.
In spite of the fact that Rocket Kitten was ousted this September, Check Point reveals that the state-sponsored hackers continued their operations regardless, making tiny changes to their malicious code and continuing to operate like nothing happened.
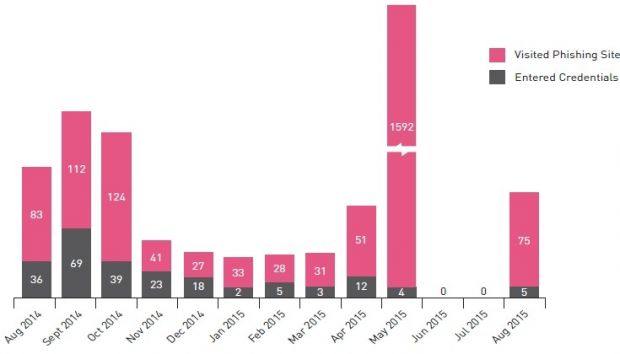
Check Point researchers got their hands on a phishing server used by Rocket Kitten
This was confirmed when Check Point researchers uncovered one of the group's phishing servers left unprotected online. Siphoning information from the aforementioned server, security researchers managed to build a complete map of previous targets, confirming Trend Micro and ClearSky's initial conclusion that the hackers have links to the Iranian government based on the spectrum of their targets.
Analyzing the information they found on the server, Check Point researchers also exposed a list of hacking and spying tools used by the hackers. These include:
- the CWoolger keylogger (written in C++)
- the .NETWlooger keylogger (written in C#)
- the FireMalv Firefox password stealer
- the Gholee malware
- the MPK RAT (remote access trojan)
- the Metasploit hacking framework
- the Hajiv & SQLMap SQL injection tools
- the Acunetix & Netsparker Web vulnerability scanner
- the WSO Web Shell PHP-based backdoor
- the NIM-Shell Perl-based backdoor
Despite the relative success Check Point had in dismantling this operation, the cyber-security vendor's researchers don't believe this is the end of Rocket Kitten.
The full "Rocket Kitten: A Campaign With 9 Lives" PDF report is available for download.

 14 DAY TRIAL //
14 DAY TRIAL //