Marie Moe, a former member of Norway's Computer Emergency Response Team, gave a talk at the 32nd Chaos Communication Congress (32C3) in Hamburg, Germany, revealing details about unsafe practices used for modern-day pacemaker devices.
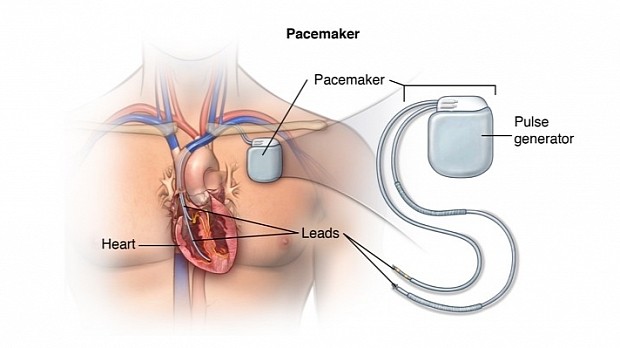
A pacemaker is a medical device implanted under a person's skin, with wiring going down to his heart, helping regulate abnormal heart rhythms.
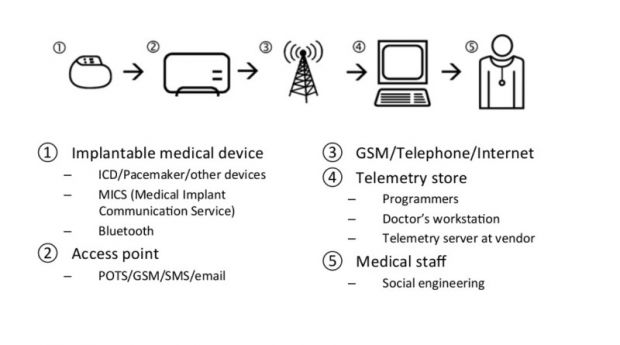
Invented in the 1920s, these devices have evolved across time, shrinking in size, and in recent years gaining more digital capabilities, especially when it comes to sending data from the patient's body to nearby equipment (called access points), or remote servers.
In today's world of IoT hacking, this can raise serious concerns if the pacemakers are not using proper security and privacy-protecting protocols.
IoT-enabled pacemakers use unencrypted communication channels
Presenting together with Eireann Leverett, ICS security researcher at Cambridge University, Mrs. Moe revealed that most pacemakers collect information about patients, and transmit it via WiFi to bed-stand access points and other medical devices used during hospital checkups.
While the latter situation is normal and expected behavior, Leverett, who helped Moe analyze the device's under-the-hood behavior, said that the bed-stand access point devices, which collect information about the patient's health while at home, uses trivial communications protocols when sending the data to remote servers.
"Yeah, you can see it's [bed-stand access point device] using famously secure methods of communications that have never been backdoored or compromised by anyone before," Leverett pointed out, referring to the device sending the patient health information via email, SMS, GSM, or POTS (Plain old telephone service). He was ironic.
"These are things that are concerning," he continued. "The data also travels often to other countries. So there are questions about jurisdiction, in terms of privacy rules."
He later went on to discuss how, if left unprotected, these details and subsequent transfer of information are part of an attack surface that someone could take advantage of to ascertain a person's health status.
Because Mrs. Moe had a pacemaker implant herself, the researchers were not interested in actually hacking the devices, due to inherent dangers, but said that this was doable, especially after they were able to buy a pacemaker programming device off eBay.
IoT devices have their advantages
"I was worried when I discovered that I had this possible connectivity to the medical Internet of Things. [...] In six years time I will have to have a replacement surgery, and I'm going to be a really difficult patient," said Mrs. Moe. "I really want to know how these devices work by then."
She also told the crowd that she's not particularly worried about being remotely assassinated via her pacemaker, but she is more afraid of software bugs. Since she's a former CERT member, we guess that she'd like to see more regulation when it comes to the new medical IoT field.
But the two researchers were not fully critical. They did acknowledge that having pacemakers that can send data via the Internet can help patients with mobility issues. They only wished that more modern technologies were used to secure communications and preserve patient privacy.
Below are Marie Moe and Eireann Leverett presenting their findings at the 32nd Chaos Communication Congress (32C3). The presentation's slides are available on Slideshare. The presentation's video and audio can also be downloaded from the Conference's website.
 14 DAY TRIAL //
14 DAY TRIAL //