Ciaran (Mak) McNally, an experienced security researcher, has detailed his experience with Pornhub's recently launched bug bounty program, and according to his story, the company is nowhere near intent on paying the maximum advertised reward of $25,000.
McNally's account of his recent dealings with Pornhub's security engineers is a story of frustration. The researcher details how he got access to many of Pornhub's internal services, but the company either paid extremely small fees or declined to pay him at all, proclaiming those services were out of the bug bounty's scope, even if common sense said they weren't.
McNally was an early participant in the company's bug bounty
The Dublin-based security expert says this all happened before the public announcement of the company's bug bounty program a few weeks back, while the program was in a closed beta, to which he was invited.
On his personal blog, McNally's revealed that he got access to a pornhubpremium.com content management system, for which he received only $750.
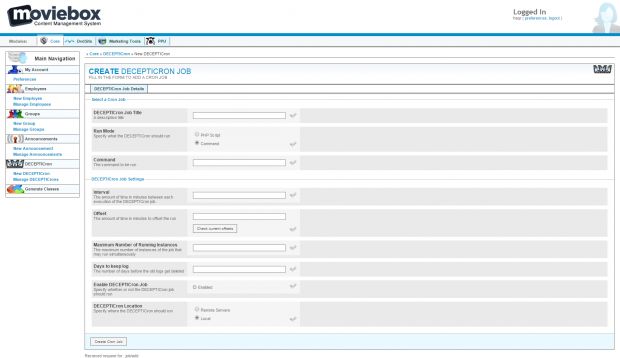
Another server he accessed included a panel called DECEPTICron for managing cron jobs across different Pornhub-owned services, for which he wasn't paid at all. Pornhub explains the server was old and soon to be decommissioned.
He then managed to get read/write access to a plethora of SVN repositories but was again paid $500, so only for a few of them, while Pornhub marked many of these out of the bug bounty's scope.
"The [SVN] code had a lot of database passwords in it for multiple sites, along with lots of juicy looking stuff," the researcher adds.
Unfortunately, Pornhub didn't reward him with the vaunted $25,000 bug reward, as it said it would in its press release, even if the researcher at that point could have entered malicious code into various Pornhub services and taken control of many of their services.
McNally also says that Pornhub also paid him $150 for a recurring XXE (XML External Entity) flaw found across multiple domains, but at this point, it was clear the service wasn't living up to other bug bounty programs ran by other companies.
Researcher says bug bounty was a way to get media attention
"It seemed to me that pornhub just marked stuff out of scope as I reported it and then narrowed their scope section on regular intervals," McNally also notes. "Now they have a public bounty and are getting a lot of media attention for being pro-security. Very disappointing and demotivational."
While everyone looked to be very optimistic about Pornhub's bug bounty program when it launched, opinions are quickly changing.
Just after the company launched its bug bounty, a hacker also contributed to this when he advertised a shell on Pornhub's servers, which he said he sold to three people.
Pornhub's answer was to call his finding a "hoax." The hacker answered Pornhub on another news site, saying Pornhub has "stupid developers who claim there [sic] server cannot execute php." After hearing of McNally's dealings with Pornhub, the same hacker tweeted yesterday, "I guess im not the only one who had problems with pornhub."
Softpedia has contacted Pornhub for comment. On Reddit, a Pornhub spokesperson provided the following statement regarding the researcher's experience with its early bug bounty:
“ Mak was invited into the program as a private beta. This has been a learning experience for us as it was our first bug bounty. As such, we truly appreciate any comments and suggestions from top researchers like him. We have made a lot of adjustments to both the program, our process for handling reports and the payout table since then. We will be releasing more detailed information on the payouts, what we consider high importance and why very soon. ”
UPDATE: Pornhub has also provided an additional statement for Softpedia, regarding the evolution of its bug bounty program ever since the early days of its program, when McNally participated."We have received thousands of submissions since we launched the program publicly. We truly appreciate the hard work of all the researchers who participated so far.
"This is our first bug bounty program and it has been quite a learning experience for us. We received a lot of constructive feedback and we wanted to address the concerns raised in those comments. We have applied the following changes to the program effective immediately:
- We have tuned the incident handling process and added more resources to the team. While some reports are more complex and might require additional processing time, we will strive to respond to every submissions within 24 hours. We have modified the payout table to better align with the other public bounty programs. We want to be fair with every researchers, and as such we have retroactively credited all past submissions according to the new payout table.
- Additionally, we have publish the payout table on the public program page to clarify what researchers should expect as an average bounty amounts for various vulnerability types.
- We have also updated the public program page to better detail what is and what is not within the scope of the bug bounty program.
- We have added Pornhub Premium to the bounty program. To be fair with everyone, all researchers who submitted a report for http://pornhubpremium.com prior to the addition of this property will also be rewarded accordingly.
- Due to popular demand, we have designed some limited edition Pornhub bug hunter t-shirts. Pornhub employees don't even have this shirt. It's only for program participants.
"We truly believe a successful bug bounty program require happy and motivated researchers. While we can’t please everyone, the feedback we received so far is quite positive and very encouraging."
 14 DAY TRIAL //
14 DAY TRIAL //