US security firm Palo Alto Networks has managed to sinkhole the C&C server infrastructure of a threat group activating from Iran's border that had focused on high-value targets all over the globe.
The company first came across the group's activities at the start of May, when it published a report on its operations, revealing malicious attacks going back to 2007, using a custom piece of spyware named Infy.
It took two tries to sinkhole the group's network
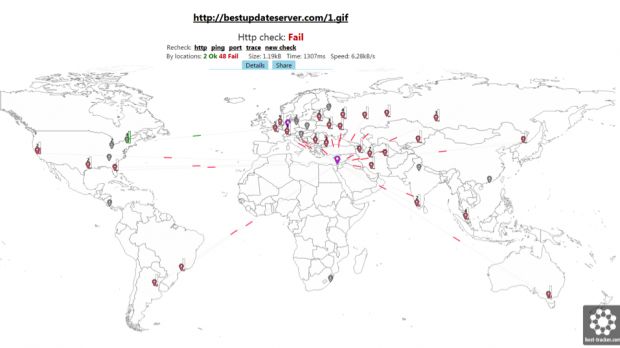
The researchers have now revealed that, with the help of the hosting companies where the Iranian APT had kept its C&C servers and domains, they were able to take over control of the cyber-espionage group's entire infrastructure.
They couldn't hijack the entire network at once, so some C&C servers remained unaffected by their initial sinkhole. As soon as the threat group lost access to some of its servers, they started pushing out a new version of their malware with their new network's C&C server IP addresses.
This didn't help them much since the security firm was able to take over these new servers as well at a later date, but the minimal changes in the malware's mode of operation revealed to Palo Alto that the crooks weren't aware that their operations were discovered.
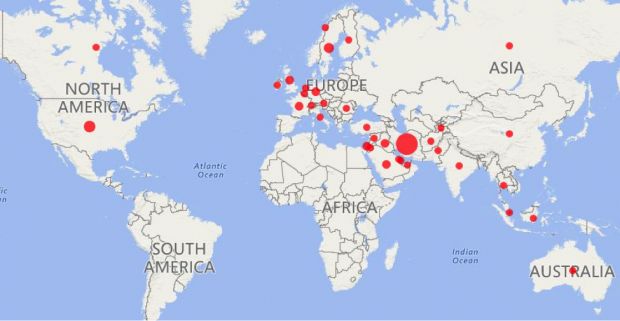
Group infected 326 targets in 35 countries
Analyzing the data found on these machines, researchers say they found 456 malware installations on 326 infected systems in 35 different countries, with at least a third located in Iran, confirming the company's initial assessment that the group is operating from this country.
Researchers also discovered that 93 percent of victims were infected with the Infy malware, and 60 percent with Infy M, a newer version of the same tool.
"The large number of victims with both variants may relate to their complimentary feature set, or represent an 'upgrade' path on victims from the original variant infection, later adding the 'M' variant as targets appeared more compelling to the attackers," Palo Alto's experts explain. "Combined with the low total number of victims, this suggests a great deal of care given to each individual campaign target."
 14 DAY TRIAL //
14 DAY TRIAL //