As the Internet of Things philosophy spreads its tentacles in all our daily used products, so will the security vulnerabilities that have affected the Internet since its beginnings.
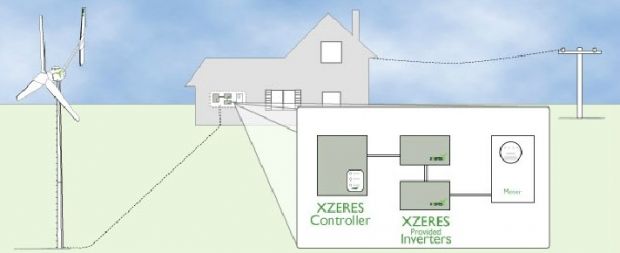
After presenting the case of a gas detector that had two critical issues in its firmware, a recent ICS-CERT advisory has now drawn our attention to the XZERES 442SR, a smart wind turbine that comes equipped with a Web-based administration panel.
According to the ICS-CERT advisory, this administration panel is vulnerable to XSS (cross-site scripting) attacks that allow even the lowest-skilled hacker to take advantage of them.
Attackers can gain admin access on affected wind turbines
"The 442SR OS recognizes both the POST and GET methods for data input," reads the ISC-CERT notice. "By using the GET method, an attacker may retrieve the ID from the browser and will allow the default user ID to be changed."
By changing the current user ID, attackers can grant themselves administrative rights, which, in turn, give them full access to the turbine's controls.
By exploiting this attack point, hackers can lower the turbine's efficiency, indirectly cutting electrical power to the systems in accordance with its power output. Depending on what kind of systems are connected to the turbine, this can be a nuisance but can also cause a loss of sensitive equipment or even human life.
Script kiddies rejoice, an IoT hack that's n00b-friendly
While ISC-CERT and the manufacturer say that there have been no attacks carried out by this technique until now, the expertise needed to exploit this flaw is at an entry level for any InfoSec researcher. The ISC-CERT experts firmly believe that there are scripts online that can be easily modified to take advantage of this flaw.
Because of the relative easiness with which this flaw can be exploited, the vulnerability, documented in CVE-2015-0985, has amassed a CVSS-v3 severity score of 9.8 out of 10.
XZERES, the US company that manufactures the wind turbine, has issued patches that need to be manually installed on each device.
Independent security researcher Karn Ganeshen is the one responsible for discovering this issue. In the past, Mr. Ganeshen discovered similar security flaws in products like routers, modems, FTP servers, and even Google Chrome.
Editor's note: The ICS-CERT listing said the vulnerability was XSS, while the CVE listing says it's CSRF. With no details on what really happens from the developer, we went with the ICS-CERT listing's description.

 14 DAY TRIAL //
14 DAY TRIAL //