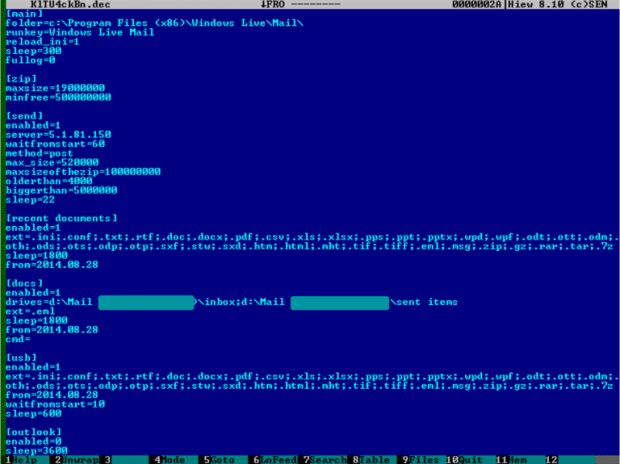
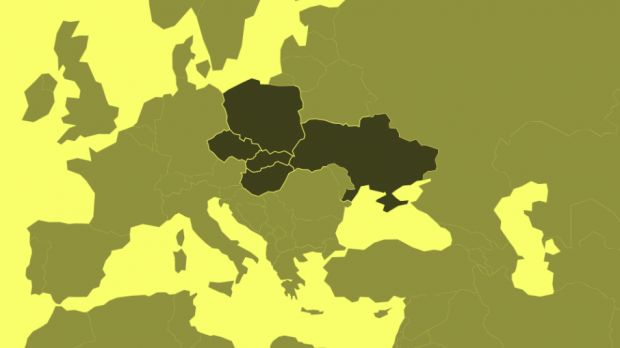
A cyber-espionage campaign targeting Eastern European government and public institutions has deployed a never-before-seen piece of malware called SBDH to infect victims and exfiltrate data.
According to Czech security firm ESET, the malware was found on infected computers in Ukraine, Poland, Hungary, Slovakia, and the Czech Republic.
SBDH malware uses simple distribution methods
The unidentified group behind this campaign is distributing the SBDH malware via spear-phishing emails. These deliver files that feature fake icons and employ the double-extension trick.
The latter is efficient because of Windows' habit of hiding a file's extension by default. This allows crooks to disguise a file like malware.doc.exe as malware.doc, fooling the user into opening an executable instead of a Word document.
After victims install this malware, SBDH will connect to its C&C server and download its two main components, one that opens a backdoor on the infected PC, and a data exfiltration module.
SBDH can steal data via HTTP, SMTP, or via emails
SBDH needs a constant Internet connection to work. By default, the malware will exfiltrate data via HTTP, but if the target has protection systems in place that prevent this, it can also steal data via the SMTP protocol, or via actual emails, with the C&C server commands and the stolen data being embedded into the content of the email.
If HTTP communications work, SBDH will use steganography to hide commands and stolen data inside JPEG or GIF files.
In case the C&C server goes down or authorities sinkhole it, the malware also includes a hardcoded URL, which points to a public blog. On this blog, there's an image that contains the address of a backup C&C server, also hidden from view using steganography.
SBDH presents similarities to the malware in Operation Buhtrap
For SBDH's data exfiltration module, the crooks behind this malware created a powerful filtering system that can allow them to decide what files to target and steal based on their extension, file size, creation date, and other criteria.
ESET's Tomáš Gardoň also noted some tactics similar to the ones used in Operation Buhtrap, when a cyber-gang stole over $25 million from 13 Russian banks.
"Using similar techniques as the malware in Operation Buhtrap, the SBDH espionage toolkit proves that even advanced threats are still being spread via simple vectors, such as malicious email attachments," Gardoň explains.
 14 DAY TRIAL //
14 DAY TRIAL //