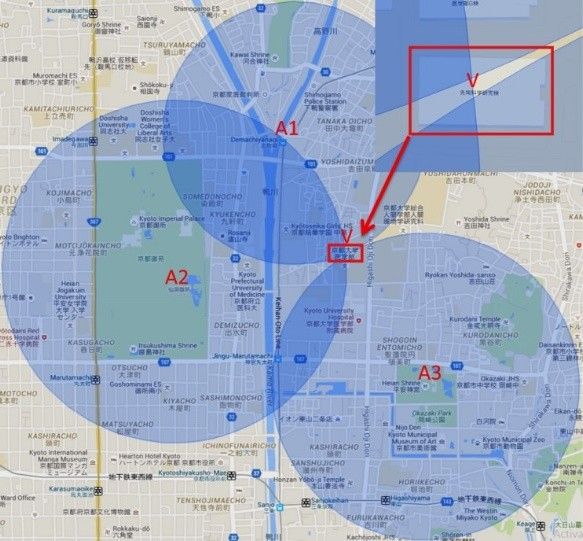
Three researchers from the Kyoto University in Japan have discovered that three of the most popular same-sex dating apps today are disclosing the user's geographical location, even if they have turned off this feature in the app's settings.
Called trilateration, or triangulation, the technique determines the location of a geographical point by the measurement of distances. If the threat actor knows the distance to a target from two different points, they can obtain two possible positions for their target. If the attacker knows the distance to a target from three separate points, they can then pinpoint their exact location.
This type of attack was already known to most dating app makers, especially the ones for same-sex dating services, which a few years back added an option in the user profile page that allowed them to hide their location.
Adapted attack method works even if users hide their location
The three Kyoto University researchers discovered that even if the app doesn't broadcast the distance anymore, it still shows partner suggestions based on their distance to the target.
By knowing this piece of information, the researchers adapted the trilateration attack into something they call "colluding-trilateration," where the attacker can estimate the target's real distance by the people between which the target appears as a suggestion for other members looking for dates.
The researchers included three apps in their study: Grindr, Jack'd and Hornet. Of all, the researchers said that Jack'd exposed the most information and was most easiest to attack.
Hornet fared the best, but despite using location obfuscation by adding noise data to the GPS data in its system, researchers said that they managed to discover the noise-adding pattern, and then conducted their attack.
Attack relies on three phones, a GPS-spoofing app, and the ability to do math
The attack is also very cheap. Researchers only needed three phones running apps that can spoof the desired GPS coordinates in order to create the three points around the target and then triangulate the user's real location. The three researchers said they used only publicly available information and basic math, with no complicated hacking techniques.
This research can prove deadly for countries actively searching for members of the LGBT community.
"Through this study, we would like to particularly alert the users of Grindr, Jack'd, and Hornet as well as the users of other LBS [Location-based Services] in general about the risk of being located easily regardless of whether the recent location anonymization and location obfuscation approaches have been adopted," researchers explained.
Researchers are trying to make services like Grindr or Jack'd update their services in order to truly hide these details, but they are also sounding the alarm for users who may be unaware that this issue exists.
More details about the attack and how the data was obtained and used can be found in the researchers' paper called: Your Neighbors Are My Spies: Location and other Privacy Concerns in GLBT-focused Location-based Dating Applications.
 14 DAY TRIAL //
14 DAY TRIAL //