Cyber-security vendor Palo Alto Networks has pulled back the curtains on a cyber-espionage campaign currently targeting Russian or Russian-speaking organizations.
As Palo Alto experts explain, this recent wave of attacks, which they detected since August and continued through December, seems to be a continuation of an older campaign that was first uncovered by ESET, an operation called Roaming Tiger [PDF].
Attackers dumped PlugX, replaced it with a custom RAT
Comparing the two distinct campaigns, there seems to be a slight evolution in the two. Both are still using spear phishing techniques to target and infect organizations, but the second wave of attacks is also using a more well-structured C&C (command and control) server structure and replacing the usage of weaponized RTF files with Word documents that leverage the Windows CVE-2012-0158 vulnerability.
This is an old vulnerability, but if the targeted system is not properly patched and updated, it can grant attackers complete control over the computer.
The malware specifically designed to leverage this vulnerability, as Palo Alto explains, is very similar to PlugX, a well-known Remote Access Trojan (RAT). Researchers have named it BBSRAT.
China is suspected, but no evidence has been found yet
PlugX has been the favorite of many APT groups linked to mainland China, but neither ESET nor Palo Alto has managed to obtain enough clues to link either Roaming Tiger or BBSRAT to China's infamous cyber-espionage activities.
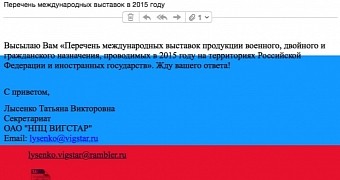
Palo Alto reports that the most high-profile case where BBSRAT was detected involved the attackers impersonating personnel from Vigstar, a Russian research organization developing satellite communications equipment for Russia's military and intelligence agencies.
"Despite the fact that the information about these attackers has been public for over a year, including a listing of many of the command and control servers, they continue to reuse much of their exposed playbook," say Palo Alto's Bryan Lee and Josh Grunzweig.
 14 DAY TRIAL //
14 DAY TRIAL //