Quiet and unknown to many users, there's a new piece of ransomware rising in the shadows. It's called WildFire and is currently spreading using the Kelihos botnet.
First signs of WildFire were discovered on June 21. According to the Cisco OpenDNS team, the crooks behind WildFire use the massive Kelihos botnet to send spam emails that contain malicious Word documents.
These documents employ social engineering tricks to convince users to enable macros in Word, which eventually allows the ransomware to take hold.
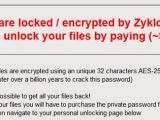
WildFire can't be decrypted
The ransomware's source code is still a mystery right now, as there are a few layers of code obfuscation researchers must go through (ConfuserEx, an unknown crypter, and then .NET Reactor), but malware analysts currently know that WildFire connects to one out of four C&C domain servers, where it registers the infection and receives a password and a user ID.
These details are used to lock the user's files, and MalwareHunterTeam tells Softpedia that "without getting the password [WildFire] it's not decryptable."
For now, users have to pay 0.5 Bitcoin (~$300) to recover their files, and as is the case with similar ransomware, payment is handled via a TOR-based website.
The Russian connection
When they inspected the WildFire C&C servers, OpenDNS researchers found comments in Russian, written in the source code of one domain, leading them to believe that a Russian-speaking crew may be behind this threat. Coincidentally, this server was set up on June 20, just one day before researchers first detected WildFire infections.
A later inspection by MalwareHunterTeam revealed that this comment was present in all four C&C domains, and even on the Tor website.
Furthermore, MalwareHunterTeam says they found the following string in an older version of the ransomware decrypter: "Алты́нного во́ра ве́шают, а полти́нного че́ствуют" [Russian: "Little thiefs are hung, but bigger thiefs are honored"].
The Cisco OpenDNS team says that, currently, the ransomware is targeting Dutch users. Such a narrow and focused targeting scheme is usually employed by crooks who run tests of their "product" before releasing it onto the whole world.
This is not the case of WildFire, which is, in fact, a finished product, according to MalwareHunterTeam, who has been taking a look at this threat in parallel to the OpenDNS team.
WildFire was previously called Zyklon and GNL
An alternative name for the WildFire ransomware is Zyklon, MalwareHunter told Softpedia. Before that, it was dubbed GNL, as in Germany and the Netherlands, the two countries it appeared to target at the time it was first spotted (April 16, 2016).
"In the time interval when we called it GNL, we saw victims only from Netherlands, and one from Canada," MalwareHunterTeam said. "As it was at the end of April, I can't tell you if it was a real victim in Canada, or just someone used a VPN for example to upload the ransom note to IDR [ID-Ransomware service]."
In fact, the country limit in Zyklon was removed at the end of May, so in theory, both Zyklon and WildFire variants have the capability to infect users all over the world.
Initially, the ransomware used to append the ".locked" extension to all encrypted files but then moved to using ".zyklon," hence its later name. "When it was using .zyklon extensions, IDR only saw victims from Netherlands," MalwareHunterTeam also added.
This doesn't mean that the ransomware's authors were targeting Dutch users, but only that Dutch users uploaded ransom notes and encrypted files to IDR in order to identify their infections. What it says is that someone was targeting these users as part of spam campaign, most likely using a batch of email addresses leaked from some sort of Dutch-based service.
There's an ongoing spam flood spreading WildFire
For earlier versions of Zyklon, the crooks used campaign IDs in the format of "nlmail22," as in Netherlands mail [number], probably to keep track of different spam runs. In WildFire, the ransomware also uses campaign IDs for each infected user.
For the latest WildFire samples, this campaign ID is "email_spread_w27," where w27 could easily stand for an incremental identifier such as WildFire 27th (spam run). An earlier tweet shows that this number is incremental, with researchers spotting a w26 campaign.
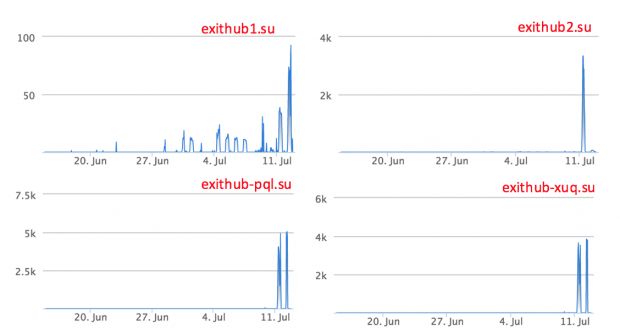
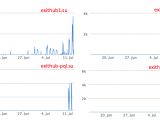
Confirming the OpenDNS report, MalwareHunterTeam says that first WildFire samples appeared around June 25, but "they started to spam more aggressively at about 5th Jul, and even more from 11th, just as the OpenDNS's graph shows."
At the time of writing, three out of four of WildFire's C&C servers are down, probably getting reconfigured for a new spam run, but definitely not down for good, since the crooks behind this campaign seem to be professionals, and not your regular script kiddies that rent ransomware for a month from RaaS services on the Dark Web.
 14 DAY TRIAL //
14 DAY TRIAL //