Dell's SecureWorks Counter Threat Unit (CTU) detected a massive phishing campaign targeting the Google accounts of military personnel, government officials, journalists and political activists in the US, EU, Russia, and former Soviet states.
The security vendor discovered the phishing campaign after it investigated the infamous hack on the Democratic National Committee server.
Just like CrowdStrike and Fidelis before it, SecureWorks discovered evidence that connected the hack to Threat Group-4127 (TG-4127), a Russian-linked cyber-espionage group also known as Fancy Bear, Sofacy, APT28, Sednit, Pawn Storm, and Strontium.
Russian APT was looking to collect Google account credentials
SecureWorks experts say the same type of phishing emails used to compromise the DNC's personnel were also used in a mass campaign that took place between March and September 2015.
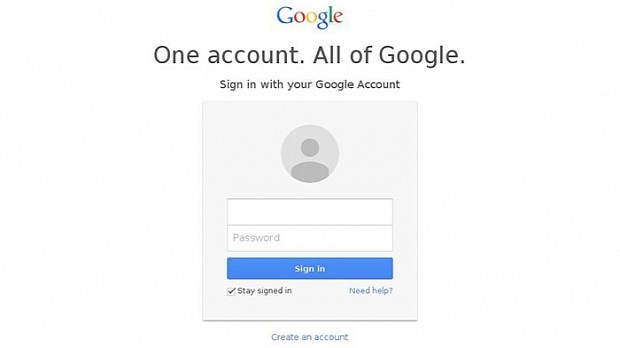
The phishing campaign used spear-phishing emails that contained Bitly links. These links were redirecting users to the accoounts-google[.]com domain (notice the extra "o").
Each Bit.ly link decompressed to a unique accoounts-google[.]com URL that contained a long Base64-encoded value at the end.
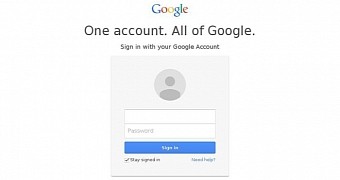
TG-4127 hackers were using these values to prefill the target's Google email address in a fake Google login page, asking the user to enter his password to continue.
Campaign targeted 1,881 Google accounts
SecureWorks says that they've detected 4,396 unique Bitly URLs as part of the campaign. Based on the URLs to which these Bitly links decompressed and the email addresses they prefilled in the phishing page, security experts say TG-4127 targeted 1,881 Google accounts.
SecureWorks says that users accessed 59 percent of the 4,396 Bit.ly links. 35 percent of the 59 percent accessed the link only once, meaning they likely entered their account password, and the campaign was likely successful. For the rest, the hackers tried numerous times to compromise the targets with subsequent spear-phishing emails, with new Bitly links.
"Of the accounts targeted once, CTU researchers determined that 60% of the recipients clicked the malicious Bitly. Of the accounts that were targeted more than once, 57% of the recipients clicked the malicious link in the repeated attempts," SecureWorks experts wrote. "These results likely encourage threat actors to make additional attempts if the initial phishing email is unsuccessful."
A focus on ... everything
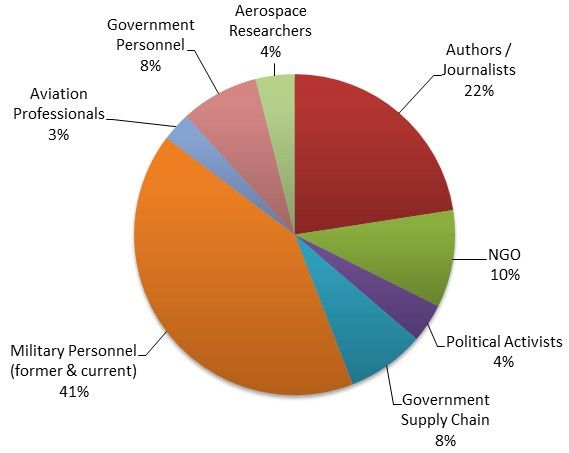
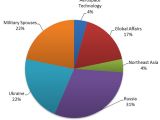
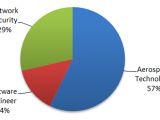
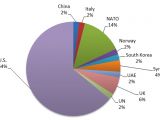
As for the targets, according to statistical data, 64 percent of all the email addresses belonged to government personnel, military personnel, government supply chain, and aerospace researchers. The rest belonged to authors, journalists, NGOs, and political activists.
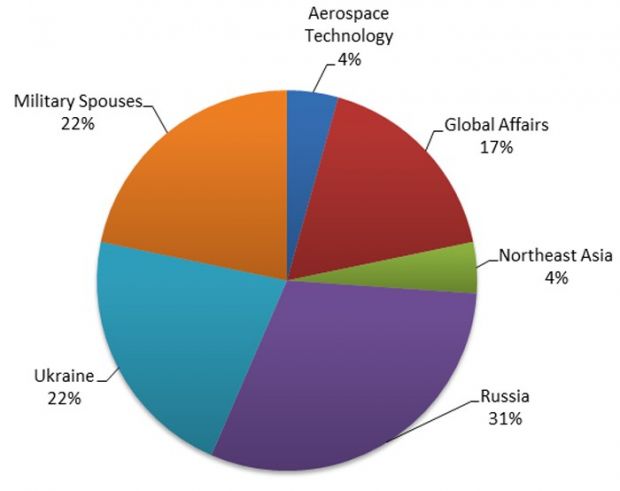
The email that received the most phishing emails belonged to a spokesperson for the Ukrainian prime minister. Most of the targets were linked somehow to Russia's military involvement in Eastern Ukraine, either as participants, reporters, or political activists.
NATO personnel was also targeted, as well as people under's Russia's influence, located in nearby former Soviet states, and in Russia's borders.
Journalists responsible for reporting about Russian politics, employees of IT and security firms, research publishers and even spouses of military personnel that like to blog were in the group's sights as well.
The massive campaign shows the lengths to which the group is willing to go to compromise its targets, sometimes through repeated attacks until the victim falls for its tricks.
 14 DAY TRIAL //
14 DAY TRIAL //