Even if it's April Fools' Day, this is no joke, as security researchers from Avira have found a new ransomware strain that goes to great lengths to provide users with all the details needed in paying the ransom.
The culprit is named Rokku (detected by Avira as TR/Genasom), and you'll be able to identify if you have been infected with this ransomware because it will encrypt all your files and append the ".rokku" extension on each file.
You may be able to brute-force the Rokku ransomware encryption key
As usual, the infection point is with spam email that comes attached with all sorts of files laced with malware. These email attachments, if downloaded and executed, will start the Rokku ransomware's encryption process, which uses a hard-to-break (not impossible) RSA-512 crypto algorithm.
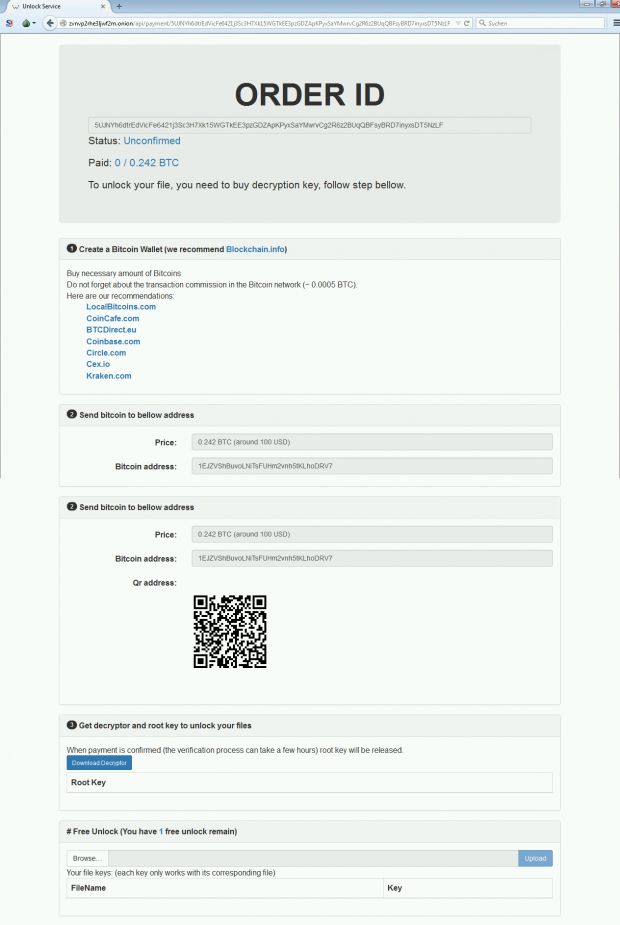
Taking into account that the ransomware asks for 0.242 Bitcoin (~$100) and that researchers have managed to crack RSA-512 keys on Amazon EC in seven hours for a cost of $107 in computational power, you may be inclined not to pay the ransom at all.
While the weak crypto (compared to other ransomware families) may be a weak point in its mode of operation, the rest of the ransomware seems to be the work of a well-versed ransomware distributor, one with experience in dealing with these types of infections and their victims.
Rokku is the work of an attentive malware developer
First and foremost, Rokku makes sure to delete shadow volume copies from your hard drive, so backup software won't be able to recover non-encrypted versions of your files. If you have backups stored offline, then you can restore them from that source. However, with no shadow volume copies, recovering them from the same hard drive is technically impossible.
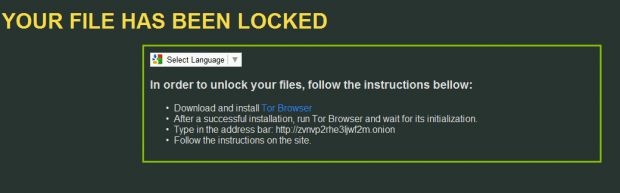
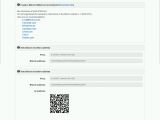
At the end of the encryption process, the ransomware drops its ransom notes, which are a text and an HTML file. Rokku author's attention to details can be seen in the HTML ransom note, which offers a Google Translate widget so that users can translate the ransom note into their own language.
While the ransom note is quite barren and only redirects users to a TOR-based website, this site is much richer in detail. Here, users can unlock a file for free to test the operational state of the author's decryption process, which doesn't always automatically work for all ransomware families.
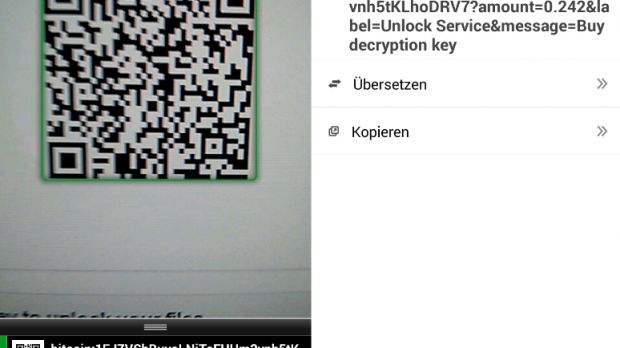
Additionally, the site lays out simple and helpful instructions through which each victim must go in order to pay the ransom. The most interesting fact is that Rokku's developer has taken extraordinary steps to make paying the ransom as easy as possible and has even included a QR code with his Bitcoin address.
Scanning this QR code with your phone would allow you to easily pay the ransom money if you have a Bitcoin wallet app installed on the device. At the time of writing, no payments have been received in the Rokku Bitcoin account, but the ransomware was only spotted for the first time on March 19, so it may not have had time to spread to a large number of victims.
Currently, its detection rate in VirusTotal is 0/57, which confirms this is a new threat, which most antivirus solutions can't pick up yet.
UPDATE: Latest VirusTotal scans reveal a detection rate of 39/57, so AV companies have started to pick up Rokku in the meantime.

 14 DAY TRIAL //
14 DAY TRIAL //