What initially looked like a string of Drupal sites infected with ransomware (that didn't work properly) now looks like a professional cybercrime operation that relies on a self-propagating Linux trojan to create a botnet with various capabilities.
Last May, in a Softpedia exclusive, Stu Gorton, CEO and co-founder of Forkbombus Labs, revealed the existence of a new type of ransomware that targeted Drupal websites. That particular ransomware wasn't really that effective, and webmasters could easily go around it and restore their old websites.
Mr. Gorton didn't share all the details with Softpedia at that particular point in time, saying there was still much to analyze about the said piece of malware that was written in Go and used CVE-2014-3704 to hijack Drupal websites.
According to new research released by Stormshield and Dr.Web, that malware, which calls itself "Rex," has received many updates in the last three months since we first reported on it.
Crooks use the Rex trojan for DDoS-for-Bitcoin extortions
The current version of the malware is still written in Go and has far more capabilities than it did in May.
The trojan can infect a lot more CMS platforms than before, it works via an advanced P2P-based botnet, it can launch DDoS attacks, it can mine for crypto-currency on infected hosts, and it can self-propagate to other vulnerable servers or devices on the local network.
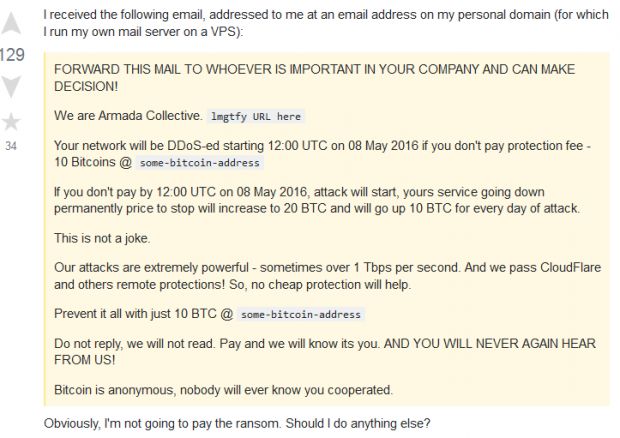
Furthermore, the crooks behind this malware have used it to threaten other webmasters with DDoS attacks unless a ransom fee was paid in Bitcoin. This StackExchange support request includes a version of the ransom note, also pictured below.
These ransom emails pretend to be from the Armada Collective gang, but nobody can validate this claim, and crooks may just be using the group's name to boost the validity of their claims.
The Armada Collective gang is a group of cyber-criminals that are famous for launching DDoS attacks unless a target pays a ransom. The group received a lot of attention in the international media, and googling their name reveals their reputation and past attacks.
Trojan can infect Drupal, WordPress, and Magento sites
On the technical side, the trojan still uses the CVE-2014-3704 Drupalgeddon vulnerability to infect Drupal sites.
This is an SQL injection flaw that allows the trojan to create an admin account through which it can control the CMS. Rex tries to lock some website pages, but as mentioned before, its ransomware capabilities are very weak.
Rex also targets WordPress sites, but it doesn't lock the sites or show a ransom note, and instead it just runs the rest of its malicious features.
For WordPress sites, the trojan tries to take advantage of security vulnerabilities in plugins such as WooCommerce, Robo Gallery, Rev Slider, WP-squirrel, Site Import, Brandfolder, Issuu Panel, and Gwolle Guestbook.
Magento sites are targeted as well, via the Shoplift RCE bugs (CVE-2015-1397, CVE-2015-1398, and CVE-2015-1399), which allow crooks access to create an admin account and control the underlying web server.
Other platforms targeted by Rex include Exagrid, Apache Jetspeed, and AirOS home routers, which the trojan targets during its initial infection process, or when it tries to replicate and self-propagate, after infecting the initial host.
Rex bots talk via a versatile and adaptable P2P system
All infected web servers are added to a decentralized P2P botnet built using the Kademlia Go library that allows developers to create apps that talk to each other via the Bittorrent DHT protocol.
P2P botnets are notorious for being hard to take down. Necurs, one of the world's largest cybercrime botnets used to distribute the Dridex banking trojan and the Locky ransomware, also uses a P2P system.
Additionally, Dr.Web researchers say they've identified Rex code that can also be used to send out spam messages.
As it stands today, the versatile Rex Linux trojan is a very lucrative malware variant, allowing crooks to earn money via Bitcoin mining, DDoS extortion, renting DDoS attacks, spam distribution, and website defacements (in case that weak Drupal ransomware actually fools anybody, which we doubt).
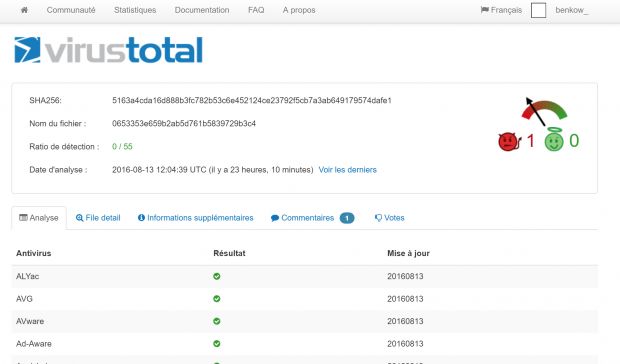
As for detection, it appears that antivirus engines on VirusTotal don't seem to recognize the trojan as a threat. Yet.

 14 DAY TRIAL //
14 DAY TRIAL //