Millions of IoT devices and HTTPS websites are vulnerable to private key attacks because of encryption key reuse, says SEC Consult in its most recent study.
The company began its survey of IoT devices by analyzing 4,000 embedded devices from 70 different vendors, ranging from simple Internet modems to Internet gateway servers.
Their research focused on public keys, private keys, and certificates found inside the firmware of these devices. Results showed that, despite the large number and the diversity of analyzed devices, 580 unique cryptographic keys were found, most being reshared among firmware images, and especially for SSH host keys and X.509 HTTPS certificates.
Crypto key reuse, the core of the problem
Using device scanning services like Scans.io and Censys.io, the researchers expanded their study to look at millions of Internet-connected devices.
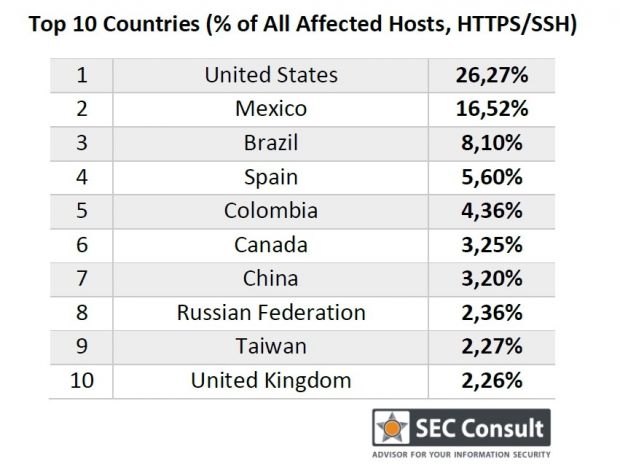
Their second stage analysis showed two interesting things. The first is that 9% of all detected HTTPS hosts on the Web shared private keys, in the form of ~150 server certificates, distributed across 3.2 million hosts.
The second thing they found was that the same issue was present for SSH keys, with 6% of all SSH hosts sharing private keys, in the form of ~80 SSH host keys, distributed across 0.9 million hosts.
While previous research into private key reuse existed, SEC Consult was able to put the blame at a vendor/product level.
According to SEC Consult, these are the companies that were found reusing encryption keys: ADB, AMX, Actiontec, Adtran, Alcatel-Lucent, Alpha Networks, Aruba Networks, Aztech, Bewan, Busch-Jaeger, CTC Union, Cisco, Clear, Comtrend, D-Link, Deutsche Telekom, DrayTek, Edimax, General Electric (GE), Green Packet, Huawei, Infomark, Innatech, Linksys, Motorola, Moxa, NETGEAR, NetComm Wireless, ONT, Observa Telecom, Opengear, Pace, Philips, Pirelli , Robustel, Sagemcom, Seagate, Seowon Intech, Sierra Wireless, Smart RG, TP-LINK, TRENDnet, Technicolor, Tenda, Totolink, unify, UPVEL, Ubee Interactive, Ubiquiti Networks, Vodafone, Western Digital, ZTE, Zhone and ZyXEL.
Internet of Things will soon become the Internet of Problems
What this means for users is that malicious parties can now carry out impersonation, man-in-the-middle or passive decryption attacks. The broad spectrum of affected devices also means that this can happen at an AS (Autonomous System) ISP level, or on your Internet-connected coffee machine that for no particular smart and explainable reason has an SSH port opened.
SEC Consult also says that many devices would not normally be vulnerable if their manufacturer did not ship them out with an open connection to the Web, which in most cases is unnecessary. These open connections allow remote attackers to use default device root credentials if not changed, and most aren't, and take over the device.
As for solutions, SEC Consult recommends that vendors use random and device-unique encryption keys for each IoT-capable device. Additionally, ISPs that have highly sensitive equipment exposed online should immediately take the necessary steps to secure them by enclosing the devices in strictly controlled VLANs.

 14 DAY TRIAL //
14 DAY TRIAL //