Researchers from InfoArmor, an Arizona-based cyber-security firm, have discovered an SQL injection flaw in the control panel of the Radamant ransomware that allows them to trick the C&C server into starting the decryption process without user interaction or without users paying the ransom.
The Radamant ransomware family was first spotted last December, when it infected its first users. Security researchers discovered that Radamant was being sold as a ransomware kit on underground hacking forums for around $1,000 per month or $100 for a 48-hours test.
Radamant v1 was cracked because it contained an encryption flaw
After Fabian Wosar, security researcher from Emsisoft, found a flaw in the encryption algorithm, he put out a decryption tool to help out infected victims. Radamant's author quickly put out a second version of his ransomware kit, which continued to make thousands of victims around the world.
Under the hood, Radamant works like most of today's crypto-ransomware families. It encrypts each file with a unique AES-256 key, which is later encrypted with an RSA-2048 master key, and then embedded in the header of each file.
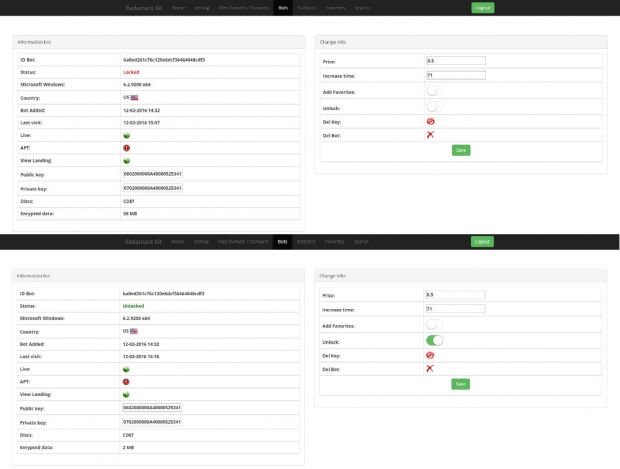
This master key is sent to the Radamant C&C server, where it's stored in the crook's MySQL database. When victims pay the ransom, the Radamant operator sends them a decryption tool, along with the RSA master necessary to unlock all files. To keep an eye on their business, the Radamant kit also comes with a Web-accessible dashboard.
Radamant v2 features an insecure control panel
InfoArmor researchers have discovered that there's an SQL injection vulnerability in the way this control panel talks with the database, which, when exploited, allows a third-party to modify the payment status of infected victims.
Whenever this status is modified, the C&C server will automatically send the decryption tool to the victim's PC, and the user can initiate the decryption process. Researchers said that the same SQL injection flaw can even be used to retrieve the entire content of the crook's database if an attacker chooses to.
InfoArmor has also noted that the developer behind the Radamant Ransomware Kit is also working on a new product called KimChenIn Coin Kit, which is malware that can steal cryptocurrency from wallet apps such as Bitcoin Core, LiteCoin Core, Dash Core, NameCoin Core, and Electrum-BTC/LTC/Dash.
 14 DAY TRIAL //
14 DAY TRIAL //