Ken Munro and Andrew Tierney of Pen Test Partners have demonstrated at the DEF CON 24 security conference in Las Vegas that it is possible to run ransomware on an IoT device such as a thermostat.
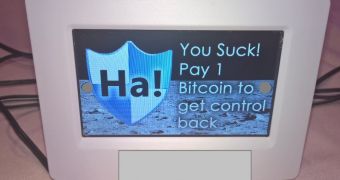
The two took an IoT thermostat that features a large screen, to show their ransom note, and hacked its underlying codebase, which was running a modified version of Linux.
Every piece of code on the thermostat ran as root
They were able to hack the thermostat because it allowed them to connect an SD card to the device.
Additionally, it seemed that every process inside the thermostat software ran with root privileges, meaning they didn't need any special privilege escalation flaws to compromise the device.
The two loaded a large 7MB JavaScript file on the device, which called some SQL commands that then allowed them to run some shell commands on the underlying Linux OS.
Because everything was executed with root privileges, the researchers had no problem bringing down the thermostat UI, locking the screen and showing a classic ransom note.
"We used an old IRC bot (Kenny in this case) and modified it a little so that it can run our various malicious scripts or shell commands," the researchers explaned. "From there, we can unlock the stat should the user decide to pay up, not that this was ever our intention!"
Installing ransomware on thermostats is quite complicated
The two acknowledged that installing the ransomware is somewhat difficult at the moment. Currently, this requires the crook to have physical access to the device or somehow trick the user into loading malicious files on the device on his own.
Munro and Tierney said it took them two evenings to hack the thermostat and that they did it just before the DEF CON conference, so they had no time to file a bug report with the thermostat manufacturer, but they plan to do so today, on Monday.
As such, they did not reveal the make and model of the hacked thermostat during their DEF CON presentation.
The most important problem the vendor has to fix is to stop code from running as root and move processes into less-privileged user accounts.
 14 DAY TRIAL //
14 DAY TRIAL // 

