Belgium security researcher Inti De Ceukelaire says that Facebook will allow anyone to query for links previously shared in private Messenger conversations.
De Ceukelaire, who was participating in the company's bug bounty program, says he informed Facebook of the issue, but it declined to fix the problem.
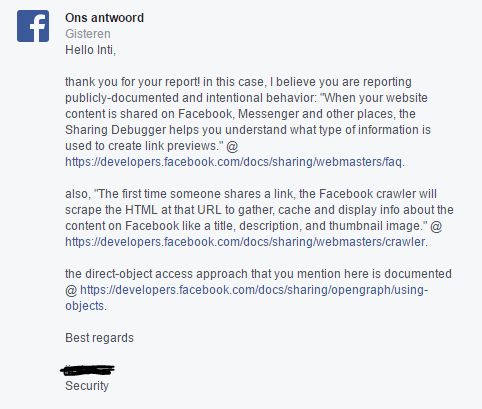
A Facebook representative told De Ceukelaire that the ability to query the Facebook Graph API and discover links previously shared on the platform was an intentional feature, and they didn't plan to restrict access to this option.
Facebook says it's intended behavior
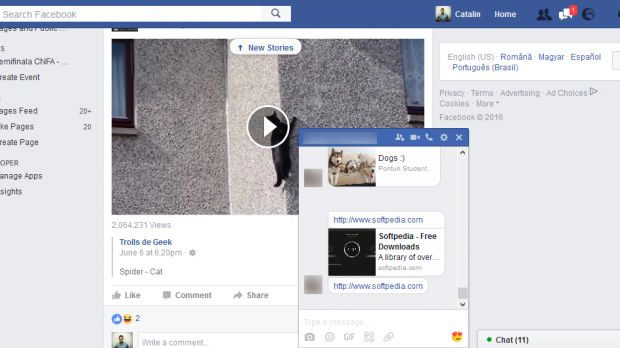
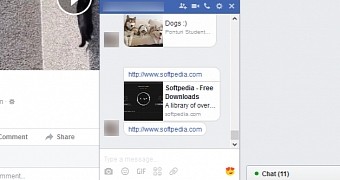
At the root of this problem is how Facebook handles links on its platform. Whenever a user shares a link on Facebook, the platform parses the link, returns the page's title, a small description, a thumbnail image, and creates an identifier (object ID), all of which are then all stored in its database.
De Ceukelaire discovered that he could query the Facebook Graph API for random object IDs and filter the responses to return only links.
The researcher says that an attacker could create a simple script that would brute-force all object IDs by incrementing their value with one and create a list of all links shared on Facebook. Obviously, a big part of these would be links shared in private conversations.
Even if there's no way to tie links to a specific user, the security researcher claims that, during the brief tests he carried out, he discovered links pointing to sensitive documents or links that inferred details about the persons who shared the URL, such as names, location, language, app data, game details, and so on.
Other links would also provide direct access to content that could be accessed only by the persons who shared the link, bypassing privacy restrictions. This included links to personal photos, secret documents shared on cloud services, or links to beta environments.
People are already suing Twitter for doing the same thing
Facebook does use rate limiting for its API platform, but there are multiple known methods through which an attacker could go around this restriction, such as VPNs and multiple access tokens.
Twitter is currently facing a lawsuit for scanning links shortened via t.co URL shortening service. Facebook is facing similar allegations for scanning private messages, but no lawsuit has been filed yet.
De Ceukelaire's discovery comes in the same week when Check Point also revealed a vulnerability in the Facebook Messenger app that enabled attackers to edit messages they previously sent, allowing them to update malicious URLs sent as part of spam or phishing campaigns. If their original website was taken down, crooks could have updated their links with new URLs if they needed. Facebook fixed this issue.
 14 DAY TRIAL //
14 DAY TRIAL //