Sergei Skorobogatov of the University of Cambridge in the UK has published new research detailing a technique that the FBI has ruled out as a viable method of bypassing the iOS passcode limit on San Bernardino's shooter iPhone.
At the start of the year, several security researchers proposed that the FBI use a technique called NAND mirroring to clone the phone's memory as many times as they want and try all the passcodes they want, until they discover the one that unlocks the phone.
The FBI said NAND mirroring wouldn't work
After the FBI abandoned any legal measures to force Apply to help it crack the San Bernardino shooter's phone, FBI Director James Comey said the agency would seek a way to hack the device using other means.
In a press conference on March 24, Comey said the NAND mirroring technique doesn't work, and several weeks later they announced they paid $1 million to a private company to hack the device.
In his researcher, Skorobogatov shows that the FBI wasn't only wrong in its assessment of NAND mirroring, but spent over $1.3 million of taxpayers' funds on something that it could have gotten for a few hundred dollars, the cost of the off-the-shelf equipment he used for his tests.
NAND mirroring works and is quite fast
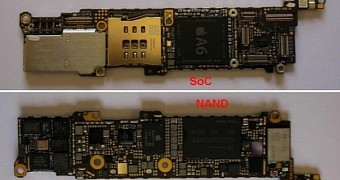
Skorobogatov was successful in implementing the NAND mirroring theory in practice. The researcher stripped down an iPhone 5c running iOS 9.3, removed the NAND Flash memory, and copied its data many times over.
He then used an automated software attack to brute-force the passcode until he found the correct code, switching between NAND Flash memory clones. Skorobogatov says that brute-forcing a four-digit code takes around 20 hours, while a six-digit code takes around three months.
"This was achieved by desoldering the NAND Flash chip of a sample phone in order to physically access its connection to the SoC and partially reverse engineering its proprietary bus protocol," the researcher explained in his paper's brief.
Skorobogatov's attack also works on iPhone 5s and iPhone 6 devices, which also use the same type of NAND Flash memory. Other iPhones use different NANDs, but the attack can be adapted.
 14 DAY TRIAL //
14 DAY TRIAL // 