Those apocalyptic Mr. Robot episodes are slowly becoming a reality as IoT devices are spreading not only in our homes but also across enterprise networks, providing access points into networks that often control critical services.
With 6.4 billion IoT devices already online, researchers estimate that over 20 billion IoT devices will be connected to the Internet by 2020.
That's why many security experts argue that now is the time to make sure that IoT security is taken seriously before it will be too late.
Of course, there are those who think it's already too late, citing the massive DDoS attacks that have pummeled OVH, KrebsOnSecurity, and most recently Dyn, all carried out with a botnet of unsecured IoT devices.
But let's not get carried away by the recent media hype. Hijacking IoT equipment for DDoS attacks is only one of the many ways attackers can use IoT devices against a target.
IoT devices are becoming Achille's heel of enterprise networks
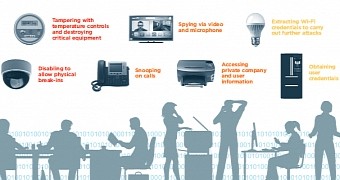
As leading IoT security firm ForeScout explains, attackers can also leverage IoT equipment as pivot points in corporate networks, using them as entry points to breach sensitive servers and steal data undetected.
Employing the service of renowned hacker Samy Kamkar, ForeScout says that it generally takes an intruder under three minutes to hack an IoT device.
In most of these cases, the vulnerability resides in the continued use of default passwords for the device's management interface. Even if the device is not exposed to the Internet, sysadmins have to change the default.
In fact, one of the best security advice is to change the default password of any device, not necessarily IoT equipment.
Even after changing default logins, IoT devices should be safeguarded
While Kamkar says that some devices might take more than three minutes to break in, hackers eventually find a security flaw which they can expose, mainly due to a lack of regulation in the IoT field, where companies aren't penalized for failing to fix their software.
This is why companies are advised to place such devices behind technologies such as firewalls, intrusion detection systems, intrusion prevention systems, or network access control systems.
While some news sites might continue to insist that DDoS attacks are the main danger from unsecured IoT devices, the truth is that DDoS attacks are the best case scenario.
For more details on some of the ways hackers can exploit IoT security flaws, you should take a look at ForeScout's IoT Enterprise Security Risk report.
“ Research Methodology: Kamkar conducted extensive research (including reviewing datasheets, previous hacks, peer-reviewed/industry research, known CVEs and first-hand conversations with industry peers) to evaluate each device, looking into vulnerabilities of the following: inputs, outputs, physical ports, communication protocols, manufacturing techniques and software and/or firmware involved. ”
 14 DAY TRIAL //
14 DAY TRIAL // 