A modification of an older Windows vulnerability can be used over the Internet and allow attackers to bypass Windows authentication, gaining control of remote computers.
Last November, Synopsys security researcher Ian Haken demonstrated how it would be possible to bypass Windows authentication and even BitLocker encryption on devices to which he had physical access.
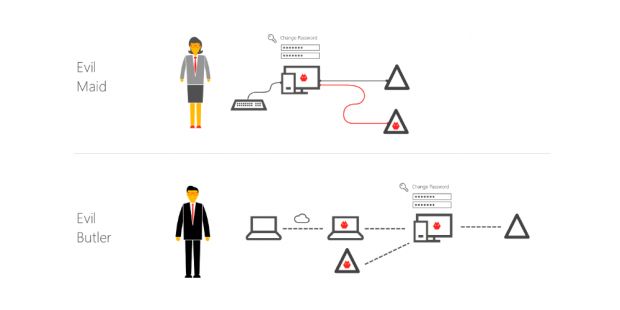
Original Evil Maid attack that bypassed Windows logon and BitLocker
The attack routine he described involved taking a computer out of the enterprise network it was assigned to and away from its original domain controller.
The attacker would set up a rogue domain controller with the same name but that used incorrect time settings, making the computer think the password's lifetime had expired.
When the attacker would connect the PC to this rogue domain, they would be asked to change the computer's password, which would also be saved in a local cache file.
The attacker would disconnect the computer from any domain controller and would be able to use the fake password they set up, which would get validated against the poisoned cache file they created with the fake domain controller.
Thus, an attacker with access to the computer would be able to bypass authentication and, inherently, BitLocker encryption.
Evil Maid attack fixed
Microsoft fixed this vulnerability (CVE-2015-6095) following Haken's research and then fixed it again when two researchers pointed out in February 2016 (CVE-2016-0049) that the fix was incomplete.
This type of attack is known in infosec circles as an Evil Maid attack because physical access is needed to compromise the device. As such, Evil Maid attacks are usually not considered dangerous.
At this year's Black Hat USA 2016 security conference that took place in Las Vegas during the past week, Microsoft security researchers Chaim Hoch and Tal Be'ery presented a variation of this attack that can be carried out over the Internet and that they called the Remote Evil Butler attack.
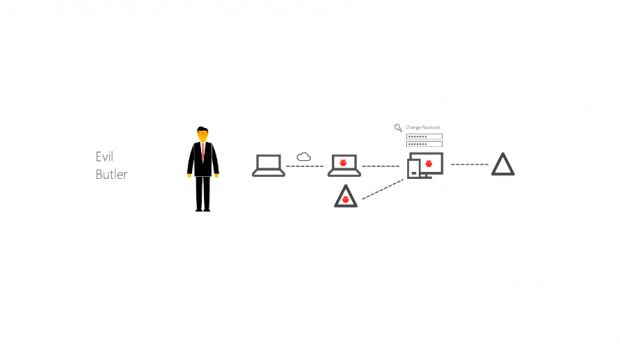
Remote Evil Butler attack
In their version of the exploit, the researchers said the attacker only needs to compromise one PC on the network assigned to a domain controller.
They install a rogue domain controller on the compromised machine. They then sniff for local machines with open RDP (Remote Desktop Protocol) connections and route their traffic towards the rogue domain controller with readily available tools.
The attackers carry out the same Evil Maid attack, but using the open RDP connection instead of the physical access required for the initial attack.
Once they have poisoned the cache, they disconnect the machine from both the rogue and actual domain controllers and extract the computer's password (NTLM hash) for the real domain controller using open source memory dumping tools (e.g. Mimikatz).
After getting their hands on the real password, attackers clean up after themselves by deleting the poisoned cache and restoring the computer to the real domain controller.
This particular attack is extremely attractive for cyber-espionage groups, who can now add a new method to their arsenal of hacking tools that will help them compromise high-value targets.
The good news is that Microsoft's February fix for the original Evil Maid attack also prevents Remote Evil Butler exploitation.
The reason the two Microsoft researchers disclosed this variation of the original attack is to make companies understand the need to keep their systems up to date at all times.
Below is a video of a Remote Evil Butler attack in action. The Hoch and Be'ery's research paper is also available, providing more details.
 14 DAY TRIAL //
14 DAY TRIAL //