A crook is hacking Internet-exposed Redis servers, adding a rogue SSH key on infected systems, deleting user data, and leaving a ransom note behind in an attempt to fool the server owner that their data was encrypted by ransomware.
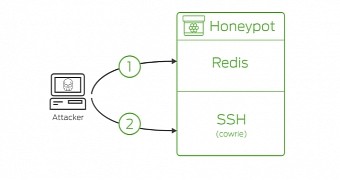
The attacker tells the Redis DB owner that they should pay a 2 Bitcoin (~$1,100) ransom to recover their files, but in reality, all the data is gone, according to a honeypot server set up by Duo Security that has captured the crook's real actions.
The return of Crackit Ryan
The problem at the core of this issue is that server owners leave crucial and very sensitive Redis databases exposed online. Duo researchers say they've found over 18,000 Redis databases available online that featured no password authentication.
Researchers claim they've identified evidence of attacks on 13,000 of these servers (around 72 percent). The evidence they're mentioning is an SSH key that the attacker has left behind after breaking into the vulnerable server.
The SSH key is named "crackit" and was found on almost all 13,000 servers. The key also has a Jabber ID attached: [email protected].
At the start of July, in a similar report, Risk Based Security discovered the same SSH key and the Jabber ID on 6,338 servers, albeit without any clues of the attacker deleting files and asking for ransom.
Based on a user comment on our story dated August 2, fake ransomware seems to have been a recent addition to the crook's mode of operation.
Some victims paid the ransom note
According to Duo, after compromising each Redis server, the crook deletes data from the /var/www/, /usr/share/nginx/, /var/lib/mysql/, and /data/ folders. Based on honeypot data, there is no attempt to encrypt any of the data, or back it up on another server.
After these operations, the crook rewrites the server's MOTD and adds a file to the server's root folder called READ_TO_DECRYPT. This ransom note points the user to a URL that contains the following ransom note (embedded below).
According to Bitcoin blockchain statistics, the crook has received three payments to the Bitcoin address listed inside the ransom note. The crook made 2.5995 Bitcoin (~$1,450).
Knowing what the hacker is actually up to, users should not pay the ransom in any way if they discover the "cracka" SSH key on their servers. Users can still recover files from off-site data stores if they regularly create backups for their servers.
UPDATE [September 1, 2016]: Lawrence Abrams of Bleeping Computer has connected the attacks on Redis servers with the attacks using the FairWare ransomware that targeted Linux web servers.
 14 DAY TRIAL //
14 DAY TRIAL //