New screen-locking ransomware posing as a Windows activation window and asking users to call a toll-free number to regain access to their PC is targeting mainly people in the US.
The ransomware was first spotted by security researcher S!Ri and then by Symantec's team, and it is not distributed en mass like other threats, with just a few infections here and there.
What makes this ransomware different are some of the details that reveal this is not your casual screen-locker ransomware bought off the Dark Web by a small-time crook, but something that was well planned in advance.
Ransomware distributed via freedownloadmanager.exe file
First and foremost, infections occur via a program called freedownloadmanager.exe, which some users might install on their computer.
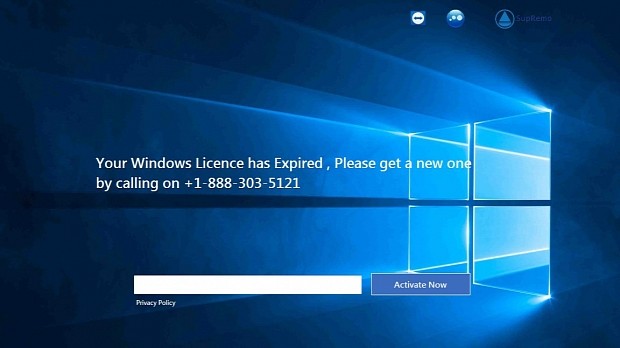
This actually installs the ransomware, which takes over the user's computer and shows a screen with the standard Windows 10 wallpaper and an input field. Above this input field is the following message:
“ Your Windows Licence has Expired, Please get a new one by calling on 1-888-303-5121 ”
Above this message are the icons of two applications, LogMeIn and TeamViewer. Both are legal and safe apps that allow someone to log onto a remote computer.The role of these shortcuts is unclear at the moment, but they might be fully working applications packed inside the ransomware that might allow a crook to log into the user's desktop to reactivate the computer when calling the toll-free number.
Nobody answers the toll-free number
This is only speculation since Symantec called the number shown on the screen, as a test, but nobody answered for 90 minutes. As such, the price it might take to unlock this type of ransomware is unknown at the moment.
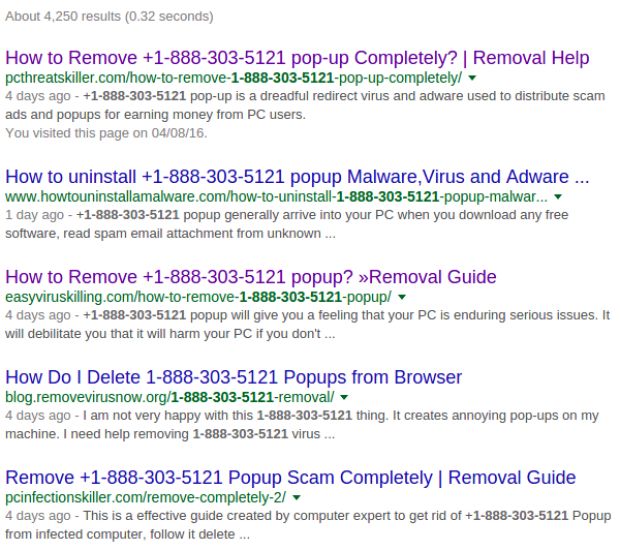
Things get weirder when searching Google for the toll-free number. This search yields a large number of results that advise users to pay the fee to get rid of the activation screen.
Symantec says that these look like poisoned search results, most likely created and promoted using black hat SEO techniques by the hackers to convince users to pay for the activation fee.
Fortunately, Symantec's developers and VMRay developer Chad Loeven have discovered that typing 8716098676542789 in the activation field will remove the ransomware.
 14 DAY TRIAL //
14 DAY TRIAL //