The website of the British Association for Counseling & Psychotherapy (bacp.co.uk) has been hit by a variant of the CTB-Locker ransomware, The Register reports.
This may be the first time that ransomware has actually defaced a website in an attempt to convince its owners to pay up the ransom demand.
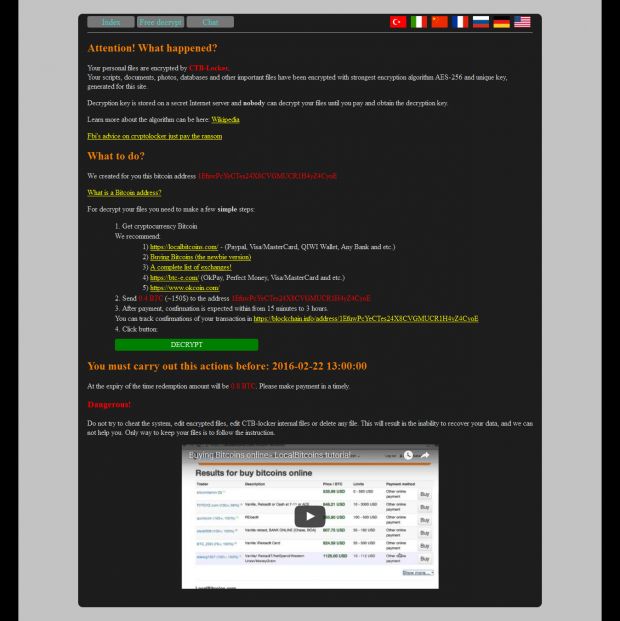
The BCAP website currently serves the standard message shown to all CTB-Locker victims, informing them that their files have been encrypted and they need to pay a ransom to a Bitcoin address before a certain deadline.
The crooks are asking for 0.4 BTC (~$150), and they have given website operators until February 22, 13:00, to pay the ransom, or the sum will double.
This doesn't look like a standard CTB-Locker infection
There are many peculiar things about this specific infection. First off, the ransomware claims to be CTB-Locker, a piece of ransomware that has infected only Windows computers until now. The BACP website is hosted on a Fedora (Linux) machine.
Additionally, CTB-Locker scrambles the file name of each file it infects, so if the infection took place on the Linux system and it was the work of CTB-Locker, then the server's index.html/index.php file would be renamed, so it wouldn't be able to deliver a homepage.
Ransomware on Linux computers has been spotted before and has been seen specifically targeting Web hosting and code repository environments. That particular piece of ransomware, called Linux.Encoder, only left boring text files behind and never bothered to create HTML ransom notes that could be used as defacement messages.
The ransomware was specifically crafted to target websites
The Register speculates that the ransomware might have been accidentally synced to the Web server after it infected one of the organization's computers.
The wording of the ransomware's defacement message makes us believe the ransomware was specifically crafted to target websites and that its defacement page was specifically built for replacing the files of locked websites.
"Your scripts, documents, photos, databases and other important files have been encrypted with strongest encryption algorithm AES-256 and unique key, generated for this site."
Notice how the last word is "site" and not "computer," the default phrasing in all standard CTB-Locker ransom notes encountered when it hits workstations, personal desktops, and laptops.
Are we seeing the emergence of a new ransomware class?
Moreover, The Register has noticed that the defacement page also includes three links at the end of its source code, which, when accessed, show a JSON response of {"status":"not_payed"}, referring to the fact that the BACP has not paid the ransom.
These links would be technically useless on a desktop infection and also show that the ransomware authors specifically created this "alleged" CTB-Locker variant just for infecting websites.
A more likely scenario would be if the attackers managed to gain access to the server through an exploit, ran the ransomware, and then left the defacement package behind.
The fact that some of BACP's original Web pages are still available and were skipped during the encryption shows that the ransomware may not be really that efficient as the original CTB-Locker Windows variant, but only a scanty clone that tries to leverage on a more famous "brand."
While in the past hackers that managed to break into sites would regularly steal user data and sell it on the black market, or would secretly stash malicious files somewhere on the server to use it in other attacks, we may see a new type of cybercrime business emerging. Breaking servers and leaving ransomware behind sure beats the hell out of hacktivism-related defacements or selling PII (Personally Identifiable Information) on the black market at ever-shrinking prices.
 14 DAY TRIAL //
14 DAY TRIAL //