A new ransomware variant called R980 is using the Mailinator disposable emails service to provide users with a way to interact with the ransomware's creator.
Previously today, we published a report on another new piece of ransomware, also spotted for the first time this week and called Smrss32.
In our report, we referenced that quirk that makes each piece of ransomware different and memorable among the masses of new variants that are detected each week.
While for Smrss32 this quirk was its obsession with searching and targeting for 6,674 file extension types, R980's quirk is just as strange.
R980 uses Mailinator addresses as anonymous PO boxes
Most ransomware infections do one of two things. They either provide an email address where they want users to send an email and get in contact with the crook to negotiate the ransom, or they provide a link to a TOR-based website, where the user can go, make the payment, and download a decrypter, optionally using a live chat window to talk to the crooks and ask for support.
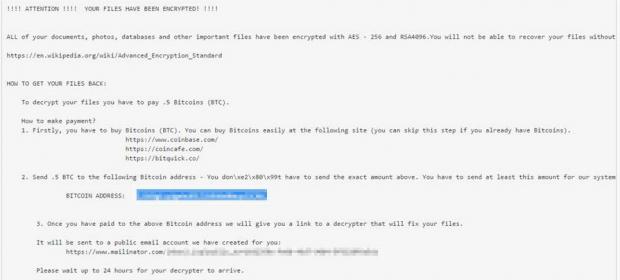
In R980's case, the crooks use the ransom note to list a one-of-a-kind Bitcoin wallet address and instruct him to make a payment to that address.
The crooks tell the user that, once the payment is made, they'll automatically detect it and send the decrypter to a disposable email address they created via the Mailinator service. This address is listed in the ransom note and is unique to each user.
Users should be very careful with R980
Infected users must be very careful because Mailinator's main feature is that it automatically deletes all emails after a few hours.
This means that, once the user has paid the ransom, they have to check the Mailinator inbox to see when their decrypter arrives or risk losing it for good, possibly losing all their files as well.
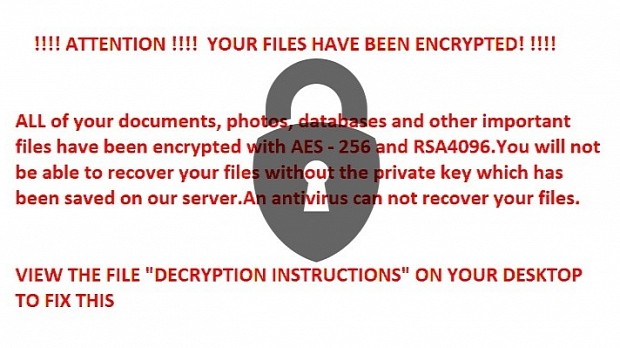
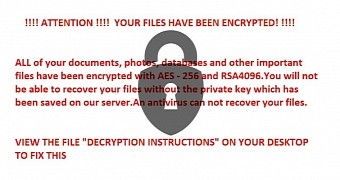
Since R980 uses a dual encryption system based on the AES-256 and RSA 4096 algorithms, there's a very small chance that security researchers might be able to crack this ransomware and create a free decrypter.
According to Trend Micro, R980 is distributed via spam email that contains Office files that ask the user to enable macro support when opened. Enabling macros (content editing) will, of course, install R980.
 14 DAY TRIAL //
14 DAY TRIAL //