LTE routers made by Quanta Computer Incorporated, a Taiwanese hardware manufacturer, are plagued by over twenty major security flaws ranging from backdoor accounts to remote code execution bugs.
Pierre Kim, an independent security researcher, came across these issues while testing devices installed with the latest firmware. According to his findings, Quanta 4G WiFi Router QDH, Quanta 4G WiFi Router UNE, Quanta 4G WiFi Router MOBILY (QDH-Mobily - CPE342X), and Quanta 4G WiFi Router Yoomee versions are affected.
Other Quanta CPE (Customer-Premises Equipment) variations that run the same vulnerable version may also be vulnerable. Based on the languages in which the help manuals are provided, the Quanta routers may be found in English, French, Chinese and Arabic-speaking countries.
Backdoor here, backdoor there, backdoors everywhere
As for the vulnerabilities, the sheer number of security flaws makes Quanta look like the worst designed router ever. Kim started by explaining that he first found hardcoded SSH keys inside the firmware, which allowed him to decipher SSH traffic coming to the router.
He then stumbled upon a few backdoors, one for the Samba service, then for the Telnet and SSH servers. Additionally, he later found that another backdoor could be started on the router in the form of a Telnet daemon if the user has turned the default one off. This backdoor can be activated by sending a simple UDP packet on a specific port.
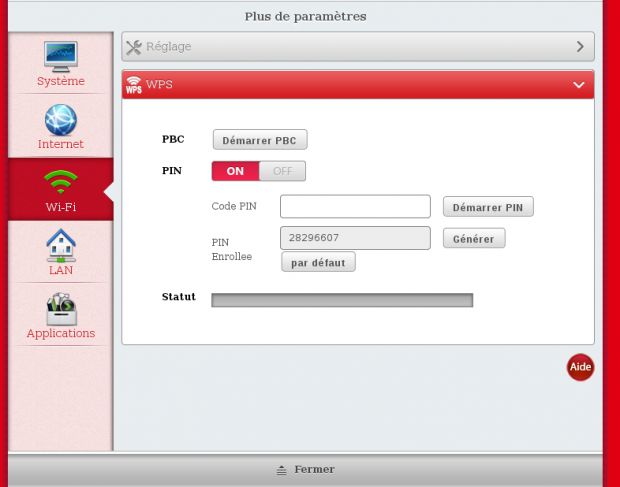
Kim also found that the router's WPS (Wi-Fi Protected Setup) also used a hardcoded PIN for setting up local Wi-Fi networks. If the user wanted to generate a random WPS PIN, then this would be created using a simple algorithm that was easy to reverse engineer, allowing attackers to guess PIN patterns.
Remote code execution (RCE) flaws and denial of service (DoS) issues were also discovered, but so were problems with FOTA (Firmware Over The Air) updates, which used expired SSL certificates and another set of weak default, hard-coded credentials to contact FOTA servers.
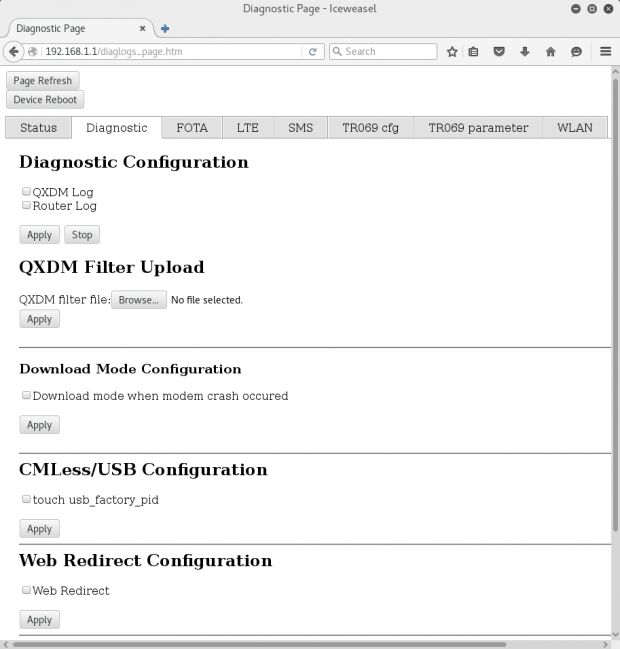
If this wasn't bad enough, the router's Web admin panel was also insecure and allowed attackers to retrieve sensible information about the device's setup. Further, the researcher also unearthed an undocumented diagnostic Web page, which also contained a plethora of sensitive information.
Other issues found in the router's firmware include arbitrary file browsing and file reading using the HTTP daemon, a hardcoded password for a No-IP account, weakness in the router's default WiFi password mechanism that allows attackers to brute-force it very easily, and the possibility to tap network traffic.
Bugs are still active, Quanta failed to fix them
The researcher says that Quanta has been told about all issues since last December, but that all vulnerabilities have remained unpatched at the time of writing.
In his bug disclosure timeline, he paints a picture of a company that just didn't care about his findings.
"A personal point of view: at best, the vulnerabilites are due to incompetence; at worst, it is a deliberate act of security sabotage from the vendor," Kim explained.
"Given the vulnerabilities found, even if the vendor changes its mind and decides to patch the router, I don't think it is even possible as it needs major rewrites in several main components."

 14 DAY TRIAL //
14 DAY TRIAL //