A set of four vulnerabilities in Qualcomm chipsets allow an attacker to gain root-level access on Android devices, which, according to the latest statistics, translates to over 900 million affected tablets and smartphones.
The four vulnerabilities have been disclosed today at the DEF CON 24 security conference in Las Vegas by a team of Check Point researchers.
The four security flaws are CVE-2016-2503 (found in Qualcomm's GPU driver, fixed in Google's Android Security Bulletin for July 2016), CVE-2016-2504 (Qualcomm GPU driver, fixed in Google's Android Security Bulletin for August 2016), CVE-2016-2059 (Qualcomm kernel module, fixed in April), and CVE-2016-5340 (Qualcomm GPU driver, fixed, patch coming in Android's September Security Bulletin).
Simple exploitation routine
All four flaws can be exploited just by installing a rogue app on your device. To carry out the exploitation routine, the attacker's app does not need any special permissions, making it more likely that users would install the app without thinking anything malicious might be hiding inside.
Any of the four flaws will allow an attacker to escalate the app's permissions from user-level to root-level, granting them full access to any phone features.
This means an attacker can download and install malware and malicious apps without any interaction from the user, all done in the phone's background.
Another reason to hate Android's security update delivery systems
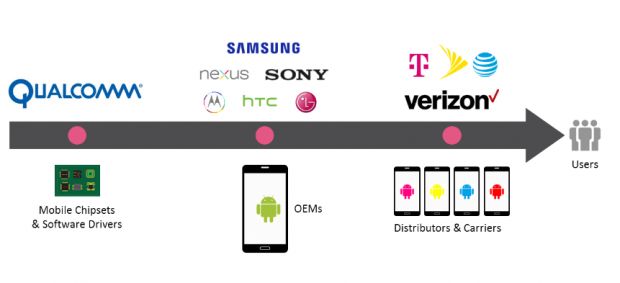
With a 65 percent market share among chipset makers for Android devices, Qualcomm chips are found in over 900 million devices.
Some of the devices affected by the QuadRooter flaw include famous models such as BlackBerry Priv, Blackphone 1, Blackphone 2, Google Nexus 5X, Nexus 6, Nexus 6P, HTC One, HTC M9, HTC 10, LG G4, LG G5, LG V10, Moto X, OnePlus One, OnePlus 2, OnePlus 3,Samsung Galaxy S7, Samsung S7 Edge, and Sony Xperia Z Ultra.
"Google (as an OEM itself, and as the maker of the Android OS) has patched 3 of the 4 vulnerabilities. The fourth patch will be part of Google’s September security updates that it makes to the Android Open Source Project (AOSP) code," a Check Point spokesperson told Softpedia.
"Qualcomm, for its part, has released all four patches to the market which fix these vulnerabilities. It’s up to the OEMs as device makers, and Google as the maker of the OS, to make sure these patches are incorporated into the Android builds they distribute – either on devices or as part of the overall AOSP."
Patching all devices will take quite some time since the Qualcomm chipset firmware patches need to be integrated by Android OEM vendors into their custom versions of the Android OS, which will then reach mobile carriers, who will decide the proper time to deliver them to end users.
Following numerous media reports, in the US, both the Federal Trade Commission (FTC) and the Federal Communications Commission (FCC) are investigating the ways in which security updates reach end users.
Check Point has prepared a technical report about QuadRooter and an Android app that will help users diagnose their phone and see if they're vulnerable.

 14 DAY TRIAL //
14 DAY TRIAL //