Security experts from SecureWorks have identified a series of incidents dating from early August 2016, where they've seen threat actors utilizing malicious PowerShell scripts to steal access credentials stored in IIS configuration files.
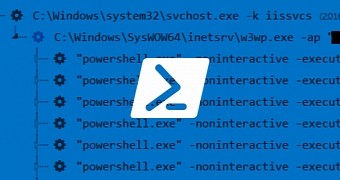
The attack occurred on an infected machine, already compromised by an attacker, who managed to save a web shell on that workstation.
The crook used this access to upload and then execute a PowerShell script that searches for web.config files, the standard filename given to Microsoft Internet Information Server (IIS) configuration files.
IIS web.config files often store credentials for other connected services as connectionStrings entries. In most cases, these are for Microsoft SQL servers, but other credentials for other services are also stored this way.
The PowerShell script would copy the content of a connectionStrings entry to the local /TEMP folder. If the data was encrypted, the PowerShell script would also use the aspnet_regiis.exe file.
The script's purpose is obviously to escalate the crook's access to other resources running on the victim's network. Crooks were most likely interested in the victim's database since that's the place where most of the valuable data is normally stored.
This is the second non-standard operational tactic observed by SecureWorks researchers, who previously detected an attacker trying to install a virtual machine on a compromised system to hide his activity inside it.
 14 DAY TRIAL //
14 DAY TRIAL //