As news about government surveillance emerged, more and more people started to direct their attention towards online tools promising privacy, causing a burst in the popularity of commercial VPN services.
VPN is used for a large number of reasons ranging from access to region-locked content, the need to protect traffic from multiple mobile devices against network sniffing or anonymity to avoiding censorship in a country.
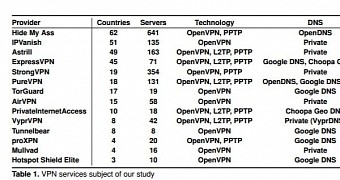
Most users trust the anonymity and protection promised by VPNs implicitly, but a research presented on Tuesday at the Privacy Enhancing Technologies Symposium shows that few of the 14 popular VPN providers analyzed maintain the integrity of the information entrusted by the user.
The researchers go on to add that info leaks refer to “all, or a critical part of the user traffic in mildly adversarial environments.” In many cases, the services rely on outdated technology (Point-to-Point Tunneling Protocol with MS-CHAPv2) that can be brute-forced.
On the same note, VPN clients leak data in networks supporting both IPv4 and IPv6 (dual-stack), and the small IPv6 traffic leaked outside the VPN tunnel could reveal the entire browsing history.
VPN products vulnerable to IPv6 leakage or DNS hijacking
Testing for IPv6 leakage, the researchers discovered that only four providers were able to maintain protection. These include Mullvad, VyprVPN, PrivateInternetAccess and TorGuard.
However, all of these were found vulnerable to DNS hijacking attempts. Out of the batch of 14, only Astrill mitigated such a risk. Basically, none of the tested services was able to offer protection against both Ipv6 and DNS hijacking.
The list also comprises services from Hide My Ass, IPVanish, ExpressVPN, StrongVPN, PireVPN, AirVPN, Tunnelbear, proXPN and HOTSPOT SHIELD Elite. They were picked based on their search ranking and the features advertised.
“All VPN services surveyed rely on the correct configuration of the operating system’s routing table. Worryingly, no attempt is made to secure this operation, for instance through monitoring the routing table to ensure that their initial configuration is not changed,” the researchers note in their paper.
The researchers involved in the study are Vasile C. Perta, Marco V. Barbera, Gareth Tyson, Hamed Haddadi and Alessandro Mei from Queen Mary University of London (QMUL) and the University of Rome. The analysis was carried out between September and December 2014.
The paper is titled "A Glance through the VPN Looking Glass: IPv6 Leakage and DNS Hijacking in Commercial VPN clients" and it is available here.
 14 DAY TRIAL //
14 DAY TRIAL //