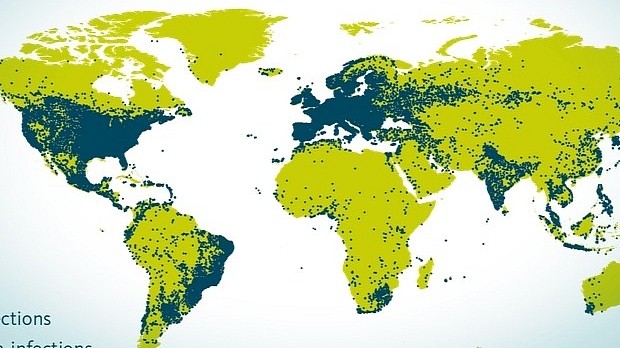
A gigantic botnet has been hiding in the shadows since 2006, and security researchers at Fox-IT are estimating that the botnet that currently has around 500,000 active bots has infected around 15 million machines during the last nine years.
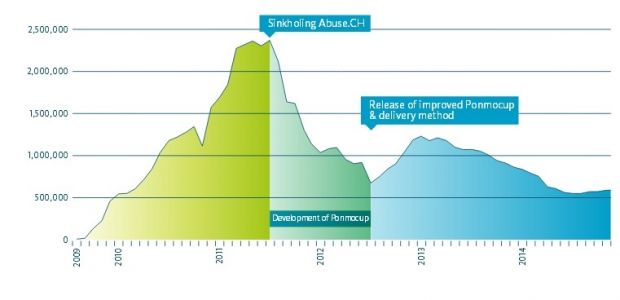
The botnet, named Ponmocup, but previously also known as Vundo or Virtumonde, was first detected in 2006, and reached its peak in July 2011, when it counted no more than 2.4 million infected systems.
While security vendors managed to sinkhole many of its bots, the botnet has assured its place in history as being one of the most long-lived, lucrative, and efficient botnets that ever existed.
Ponmocup went through over 4,000 different versions
Ponmocup's operators only targeted Windows machines, and across time, they developed over 4,000 variants for their bots, and 25 different plugins that allowed them to diversify the botnet's capabilities.
Its attack arsenal includes the ability to inject itself into Windows processes, become persistent on infected hosts, alter registry information, carry out encrypted communications with its C&C, and load other botnet modules.
Fox-IT researchers say the botnet is mainly run for financial gain and estimate Ponmocup as being a multi-million dollar business for the criminal group behind it.
"There are multiple reasons to assume this is the case. Firstly, their infrastructure is complex, distributed and extensive, with servers for dedicated tasks," says the Fox-IT staff.
"Secondly, they operate, maintain and monitor their comprehensive infrastructure with a group of operators and are quickly able to mitigate potential risks that are discovered. Thirdly, the malware itself is sophisticated and aimed at avoiding detection and analysis," Fox-IT noted.
Ponmocup, the work of a Russian cyber-crime group
The security researchers also claim the botnet is run by Russian-speaking operators, basing their theory on the fact that most instructions, tutorials, and affiliate programs that surround Ponmocup is all written in Russian.
Additionally, Ponmocup operators seem to have kept the botnet out of the territories of post-Soviet states, a tactic also employed by other cyber-criminal groups, mainly to avoid annoying Russia's cyber-crime fighting units.
The modus operandi of this huge botnet has been documented in depth by security analysts from Fox-IT in their Ponmocup - A giant hiding in the shadows 40-page report.
 14 DAY TRIAL //
14 DAY TRIAL //